Fully updated to cover the latest security issues, 24 Deadly Sins of Software Security reveals the most common design and coding errors and explains how to fix each one-or better yet, avoid them from the start. Michael Howard and David LeBlanc, who teach Microsoft employees and the world how to secure code, have partnered again with John Viega, who uncovered the original 19 deadly programming sins. They have completely revised the book to address the most recent vulnerabilities and have added five brand new sins. This practical guide covers all platforms, languages, and types of applications. (more…)
Category: EDITORIAL
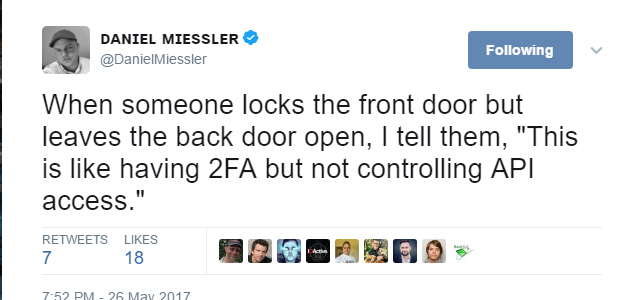
APIs are 2FA Backdoors
It’s time we accept as an industry that API keys and secrets are essentially usernames and passwords, except they’re designed to be used in an automated way to perform your company’s most sensitive functions, often instrumented by developers who don’t prioritize security.
They’ll probably respond, “Of course.”
Now ask them what you can do with that API.
“Oh, it’s a great API. You can do pretty much everything.”
“Great. How many people have access?”
“It’s super popular. We give access to all our developers, and any account can ask for and receive a key.”
“Cool. So how many of those keys are out there, and how do you control them?”
“…”
Exactly.
API keys often have full access to the platform, and guess what the access method is: a string of characters for your key, and a string of characters for your secret.
Sound familiar? How is this different from a username and password?
“Oh, but this is different because it’s all code-ey and stuff. Lots of programming and hard things.”
No.
That’s not a defense. Good APIs also share something else: great documentation.
It’s easy to do things like adding users, adjusting permissions, or pulling data using this interface because it’s meant to be easy. In fact, the easier it is to do something powerful, the better.
And this is all happening on 2FA-enabled accounts, despite that supposed higher level of security.
Summary
- Everyone understands that 2FA is better than just a username and password.
- Everyone is also trying to add an API to their new services.
- API keys are just usernames and passwords used in code.
- Few people realize this, and think it’s safe because “programming is hard” or because “APIs are magic.”
- APIs are not magic. They’re an entry point into your application, and there are far too many keys and secrets floating around Slack, Github, and many other places on services that are 2FA-enabled.
- This presents a false sense of security.
2FA is great. Enable it where you can. But it’s not the end of the conversation. Be sure to look at your API as well. Know what you can do with it, know who has keys, know how often they expire, and have a plan for monitoring and response.
For all intents and purposes, you should treat API access like legacy username and password access. After all, API keys and secrets are credentials.
Credentials can be stolen, and credentials can be used to do bad things.
This post is adapted from Daniel Miessler’s original blog post, which you can find at https://danielmiessler.com/blog/apis-2fas-achilles-heel/.
Five Reasons Why You Should Go To BruCON
BruCON is one of the most important security conferences in Europe. Held each October, the ‘Bru’ in ‘BruCON’ refers to Brussels, the capital of Belgium, where it all started. Nowadays, it’s held in the beautiful city of Ghent, just 55 mins from its origin. I had the chance to attend this year, and here are the five things that make it a great conference, in my opinion.
(Shyama Rose talking about BASE jumping and risk)
While paid trainings take place two or three days before the conference, free workshops are available to the public during the two-day conference.
«Escalating Privileges Through Better Communication»)
Black Hat and DEF CON: Hacks and Fun
The great annual experience of Black Hat and DEF CON starts in just a few days, and we here at IOActive have a lot to share. This year we have several groundbreaking hacking talks and fun activities that you won’t want to miss!
For Fun
Join IOActive for an evening of dancing
6–9PM
House of Blues
Bally’s penthouse suite
10PM till you drop
Bally’s BLU Pool
Escape to the IOAsis – DEF CON style!
12–6PM
Bally’s penthouse suite
Robert Erbes: Little Jenny is Export Controlled: When Knowing How to Type Turns 8th-graders into Weapons
DEF CON: 2PM Saturday, August 8, 2015
DEF CON: 4PM Saturday, August 8, 2015
Not only will we reveal new vulnerabilities, along with the methods and techniques for finding them, we will also share defensive techniques and mitigations that can be applied now, to protect against the average 1-3 year patching lag (or even worse, “forever-day” issues that are never going to be patched).
I illustrate these concepts using several case studies. In each, the act of assessing the network revealed information to the client that was unexpected, and valuable, “beyond the scan.”
DEF CON: 2PM Saturday, August 8, 2015
XSLT is used to manipulate and transform XML documents. Since its definition, it has been implemented in a wide range of software (standalone parsers, programming language libraries, and web browsers). In this talk I will expose some security implications of using the most widely deployed version of XSLT.
Black Hat: 9AM Thursday, August 6, 2015
DEF CON: 6PM Friday, August 7, 2015
Kenneth will host a table in the IoT Village at DEF CON where he will present a demo and explanation of vulnerabilities in the US electric grid.
Black Hat: 5:30PM Wednesday, August 5, 2015
DEF CON: 2PM Saturday, August 8, 2015, IoT Village, Bronze Room
Satellite receivers are massively joining the IoT and are used to decrypt pay TV through card sharing attacks. However, they are far from being secure. In this upcoming session we will discuss their weaknesses, focusing on a specific attack that exploits both technical and design vulnerabilities, including the human factor, to build a botnet of Linux-based satellite receivers.
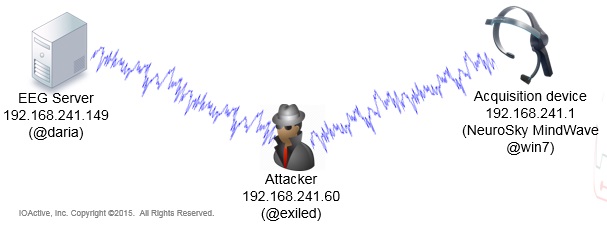
Electroencephalography (EEG) is a non-invasive method for recording and studying electrical activity (synapse between neurons) of the brain. It can be used to diagnose or monitor health conditions such as epilepsy, sleeping disorders, seizures, and Alzheimer disease, among other clinical uses. Brain signals are also being used for many other different research and entertainment purposes, such as neurofeedback, arts, and neurogaming.
I wish this were a talk on how to become Johnny Mnemonic, so you could store terabytes of data in your brain, but, sorry to disappoint you, I will only cover non-invasive EEG. I will cover 101 issues that we all have known since the 90s, that affect this 21st century technology.
Lawsuit counterproductive for automotive industry
It came to my attention that there is a lawsuit attempting to seek damages against automakers revolving around their cars being hackable.
The lawsuit cites Dr. Charlie Miller’s and my work several times, along with several other researchers who have been involved in automotive security research.
I’d like to be the first to say that I think this lawsuit is unfortunate and subverts the spirit of our research. Charlie and I approached our work with the end goals of determining if technologically advanced cars could be controlled with CAN messages and informing the public of our findings. Obviously, we found this to be true and were surprised at how much could be manipulated with network messages. We learned so much about automobiles, their communications, and their associated physical actions.
Our intent was never to insinuate deliberate negligence on the part of the manufacturers. Instead, like most security researchers, we wanted to push the boundaries of what was thought to be possible and have fun doing it. While I do believe there is risk associated with vehicle connectivity, I think that a lawsuit can only be harmful as it has the potential to take funds away from what is really important: securing the modern vehicle. I think any money automobile manufacturers must spend on legal fees would be more wisely spent on researching and developing automotive intrusion detection/prevention systems.
The automotive industry is not sitting idly by, but constantly working to improve the security of their past, present, and future vehicles. Security isn’t something that changes overnight, especially in the case of automobiles, which take even longer since there are both physical and software elements to be tested. Offensive security researchers will always be ahead of the people trying to formulate defenses, but that does not mean the defenders are not doing anything.
While our goals were public awareness and industry change, we did not want change to stem from the possible exploitation of public fears. Our hope was that by showing what is possible, we could work with the people who make the products we use and love on an everyday basis to improve vehicle security.
– cv
Life in the Fast Lane
- Why dedicate an entire service offering to vehicles and transportation?
- A brief history of vehicle security research and why it has been relatively scarce
- Why we believe that protecting vehicles and their supporting systems is of the utmost importance
- IOActive’s goals for our Vehicle Security Service offering
Additionally, I’ll make sure to save sufficient time for Q&A to field your questions. I’d love to get as many questions as possible, so don’t be shy.
I look forward to your participation in the webinar on February 5,2015 11 AM EST.
Upcoming Blackhat & DEF CON talk: A Survey of Remote Automotive Attack Surfaces
Hi Internet,
Chris Valasek here; you may remember me from such movies as ‘They Came to Burgle Carnegie Hall’. In case you haven’t heard, Dr. Charlie Miller and I will be giving a presentation at Black Hat and DEF CON titled ‘A Survey of Remote Automotive Attack Surfaces’. You may have seen some press coverage on Wired, CNN, and Dark Reading several days ago. I really think they all did a fantastic job covering what we’ll be talking about.
We are going to look at a bunch of cars’ network topology, cyber physical features, and remote attack surfaces. We are also going to show a video of our automotive intrusion prevention/detection system.
While I’m sure many of you want find out which car we think is most hackable (and you will), we don’t want that to be the focus of our research. The biggest problem we faced while researching the Toyota Prius and Ford Escape was the small sample set. We were able to dive deeply into two vehicles, but the biggest downfall was only learning about two specific vehicles.
Our research and presentation focus on understanding the technology and implementations, at a high level, for several major automotive manufacturers. We feel that by examining how different manufacturers design their automotive networks, we’ll be able to make more general comments about vehicle security, instead of only referencing the two aforementioned automobiles.
I hope to see everyone in Vegas and would love it if you show up for our talk. It’s at 11:45 AM in Lagoon K on Wednesday August 6.
— CV
P.S. Come to the talk for some semi-related, never-before-seen hacks.