What?
IOActive has a renowned history of uncovering security vulnerabilities in information technology platforms and devices. Our clients frequently ask our consultants to evaluate new products and technologies on their behalf. Our research teams regularly evaluate new devices and software.
As a result, IOActive often discovers new bugs and vulnerabilities in third-party products, which can have a damaging impact on our clients’ security if the vulnerable vendors do not fix these issues in a timely manner.
In order to ensure clients, businesses and vendors resolve this issue by:
- Informing vulnerable vendors of newly discovered vulnerability before publishing advisories that contain vulnerability details
- Releasing tools and proof-of-concept examples that vulnerable clients can, in turn, use to better secure their environments in the absence of vendor fixes
How?
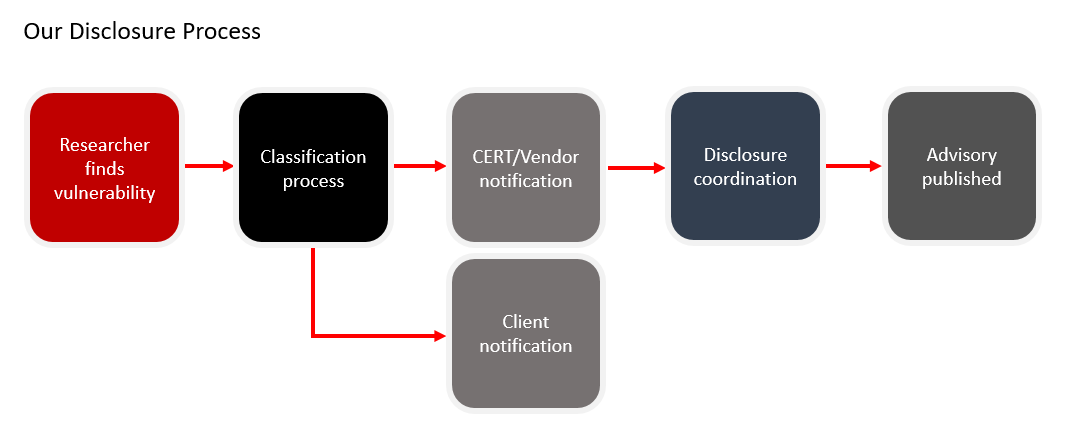
Vulnerabilities uncovered by IOActive consultants during a paid client engagement are the property of the client. This typically extends to scripts, tools, and proof-of-concept example exploits created specifically for the client and used to locate or demonstrate the exploitability of the vulnerability. IOActive also manages the coordination of vulnerability disclosure with third-party vulnerable vendors on the behalf of our clients when applicable.
IOActive notifies affected vendors about identified vulnerabilities as we identify them during our research, and act on the behalf of clients to report vulnerabilities during an engagement.
IOActive will work with the vulnerable vendor to define a course of action for remediation and will determine a future disclosure date for publishing a security advisory and related tools, PoCs, and so on, pending a case-by-case review. CERT Notification is typically done by the vendor, but in some cases IOActive will file on their behalf. IOActive can move a disclosure date to an earlier or later date, depending on specific circumstances, such as:
- A vulnerability is exploited in the wild.
- Vulnerability information is made publicly available by a third-party.
- Fixes are particularly difficult to build.
- A vendor is nonresponsive after exhaustive efforts to engage them in developing a fix.
When?
IOActive can release a security advisory and CERT notification containing vulnerability details and related tools, PoCs, and so on if:
- The vendor is nonresponsive.
- The vulnerability is already exploited in the wild.
- The vulnerability information is already publicly available.
The amount of details IOActive releases about a security advisory depends on the criticality and impact of the vulnerability
IOActive reserves the right to privately share vulnerability discoveries made during independent research at any time with customers or other third parties in order to help secure systems from attacks.

