Here’s a script I wrote to extract information from the Bluetooth metadata in an object’s memory. The script makes use of the Frida instrumentation framework, and I’ll take a little time to explain a simple scripting methodology/thought framework for solving problems with Frida.
What you will need:
- Frida Server for your device https://www.frida.re/docs/installation/
- Frida script to run https://github.com/IOActive/BlueCrawl
- Target Android phone (preferably with root permissions)
Getting Started: Your first Script
Frida forwards APIs that wrap Java objects and introduce means to inspect them, modify them, or replace them. This API is implemented in JavaScript, so you have the advantage of anonymous functions and plenty of hook/callback-style API design.
The first useful call you need is Java.perform(function(){}). Here’s an example usage:
hello-world.js:
1 setTimeout(function(){
2 Java.perform(function(){
3 console.log("hello world!");
4 });
5 });
This is essentially a “hello world” Frida Script. We’re passing the setTimeout method in JavaScript for another function, Java.perform, which itself takes a function as an argument. We’re calling the console objects log method and passing it a string; we need to use the setTimeout method because it enables our actions in the JavaScript runtime. We need the Java.perform call because it enables our actions in the Frida Java runtime which inherits and mirrors from the actual runtime we’re targeting on the Android device.
To get it up and running, just grab the Frida server for your device, pop it on the disk and fire off the script from a non-mobile computer (this is essentially the Frida client, since the server runs on the mobile phone):
bullhead:/data/local/tmp # ./frida-server-12.1.0-android-arm64
_
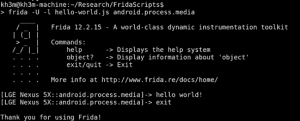
You should see your terminal spit out a “hello world” string.
Now we can make use of other Java features from within the function to which we pass the Java class in the Frida runtime. We can do stuff like search through loaded classes and pull out an instantiated version of those classes, replace loaded instances with others, and more.
Here’s a quick example showing all of the loaded classes in the current application:
1 setTimeout(function (){
2 Java.perform(function (){
3 console.log("\n[*] enumerating classes...");
4 Java.enumerateLoadedClasses({
5 onMatch: function(_className){
6 console.log("[*] found instance of '"+_className+"'");
7 },
8 onComplete: function(){
9 console.log("[*] class enuemration complete");
10 }
11 });
12 });
13 });
When you run it, it should produce the following output:
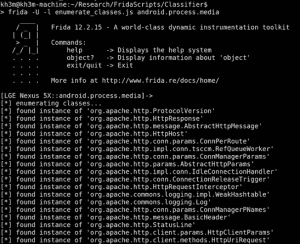
In this example, we’re running Frida against the Android media service.
Another cool thing you can do is inspect Bluetooth specific classes. This is where BlueCrawl comes in: it basically searches through all the loaded classes and pulls out those with interesting Bluetooth information. Check out this example, showing all the devices dumped from a Bluetooth scanner app’s memory:
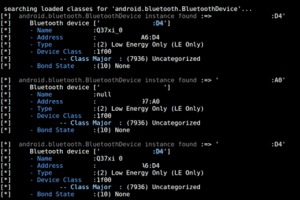
I’ve redacted the MAC addresses since some of these devices might not belong to me. 🙂
BlueCrawl also dumps information about Bluetooth sockets, and can actually show you the type of device and MAC address connected to it:
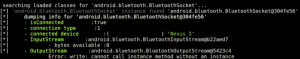
The current version’s features also include the ability to see:
- loaded
Bluetoothclasses - loaded
BluetoothSocketandBluetoothServerSocketobjects - loaded Bluetooth Device objects in memory, as stated above
I kept the features tight and as properly implemented as I could for the first iteration, so while it’s not a swiss army knife just yet, you should try this script for checks to determine whether:
- Your Bluetooth spoofing tech is working properly
- Apps are secretly scanning for Bluetooth devices
- Apps are stealing Bluetooth information
More features are on the way once I get to know Frida a little more and finish some further testing.
Happy Scripting!
References and Reading

