Tag: charlie miller
Upcoming Blackhat & DEF CON talk: A Survey of Remote Automotive Attack Surfaces
Hi Internet,
Chris Valasek here; you may remember me from such movies as ‘They Came to Burgle Carnegie Hall’. In case you haven’t heard, Dr. Charlie Miller and I will be giving a presentation at Black Hat and DEF CON titled ‘A Survey of Remote Automotive Attack Surfaces’. You may have seen some press coverage on Wired, CNN, and Dark Reading several days ago. I really think they all did a fantastic job covering what we’ll be talking about.
We are going to look at a bunch of cars’ network topology, cyber physical features, and remote attack surfaces. We are also going to show a video of our automotive intrusion prevention/detection system.
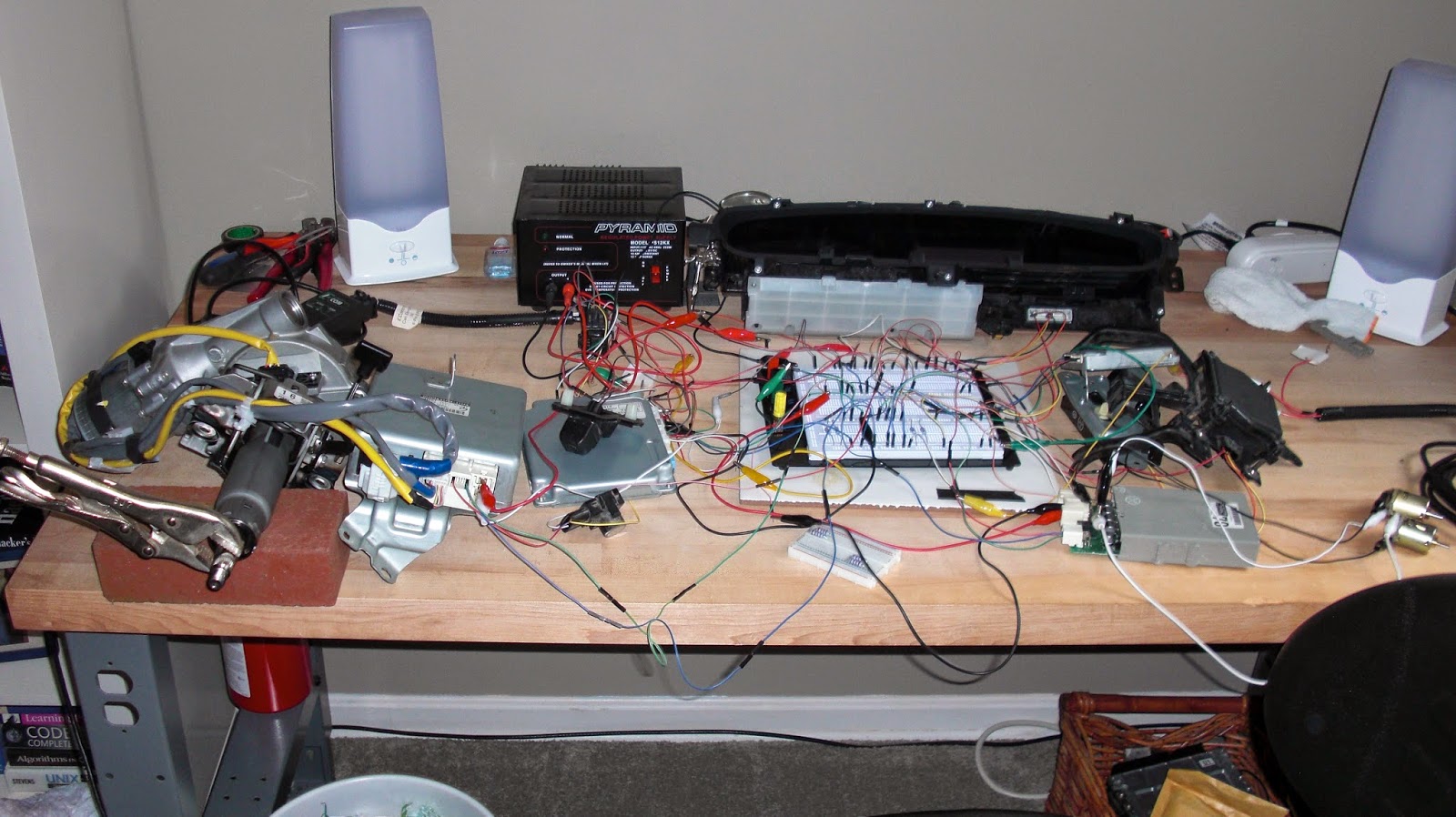
While I’m sure many of you want find out which car we think is most hackable (and you will), we don’t want that to be the focus of our research. The biggest problem we faced while researching the Toyota Prius and Ford Escape was the small sample set. We were able to dive deeply into two vehicles, but the biggest downfall was only learning about two specific vehicles.
Our research and presentation focus on understanding the technology and implementations, at a high level, for several major automotive manufacturers. We feel that by examining how different manufacturers design their automotive networks, we’ll be able to make more general comments about vehicle security, instead of only referencing the two aforementioned automobiles.
I hope to see everyone in Vegas and would love it if you show up for our talk. It’s at 11:45 AM in Lagoon K on Wednesday August 6.
— CV
P.S. Come to the talk for some semi-related, never-before-seen hacks.
Car Hacking 2: The Content
Car Hacking: The Content
DefCon 21 Preview
“Adventures in Automotive Networks and Control Units” (Track 3)
(https://www.defcon.org/html/defcon-21/dc-21-schedule.html)
- We will briefly discuss the ISO / Protocol standards that our two automobiles used to communicate on the CAN bus, also providing a Python and C API that can be used to replicate our work. The API is pretty generic so it can easily be modified to work with other makes / models.
- The first type of CAN traffic we’ll discuss is diagnostic CAN messages. These types of message are usually used by mechanics to diagnose problems within the automotive network, sensors, and actuators. Although meant for maintenance, we’ll show how some of these messages can be used to physically control the automobile under certain conditions.
- The second type of CAN data we’ll talk about is normal CAN traffic that the car regularly produces. These types of CAN messages are much more abundant but more difficult to reverse engineer and categorize (i.e. proprietary messages). Although time consuming, we’ll show how these messages, when played on the CAN network, have control over the most safety critical features of the automobile.
- Finally we’ll talk about modifying the firmware and using the proprietary re-flashing processes used for each of our vehicles. Firmware modification is most likely necessary for any sort of persistence when attempting to permanently modify an automobile’s behavior. It will also show just how different this process is for each make/model, proving that ‘just ask the tuning community’ is not a viable option a majority of the time.