Ransomware attacks have boomed during the last few years, becoming a preferred method for cybercriminals to get monetary profit by encrypting victim information and requiring a ransom to get the information back. The primary ransomware target has always been information. When a victim has no backup of that information, he panics, forced to pay for its return.

Edited from original image by Kiyoshi Ota/Bloomberg
Robots currently exist in homes, education centers, businesses and industrial facilities – as toys, companions for the elderly, customer assistants, and healthcare attendants. This trend will continue as robots occupy a dizzying array of service roles – home and business assistants, intimate physical companions (sex robots), manufacturing workers (industrial robots, cobots), law enforcement, and more.
As human-robot interactions evolve, new attack vectors emerge and threat scenarios expand. To be prepared for these future threats, we should understand the key elements needed for ransomware for robots to succeed. Most importantly, we should understand an attacker’s motivations and strategies.
Our 2017 Robot Hacking Research
Strategies in Ransomware for Robots
While robots handle different types of valuable data, they aren’t commonly used to store it. Sensitive in-transit information that is not always persisted on a robot’s internal storage includes the following:
- High definition video feed
- Audio captured by 2 to 4 directional microphones
- Payment information or other customer and business information
SoftBank’s Pepper and NAO Robots
SoftBank’s Pepper is one of the most used business oriented robots in the world – 20,000 in use in 2,000 businesses worldwide. NAO is one of the most used research and education robots in the world – 10,000 in use worldwide. Sprint has started using Pepper to assist customers at the telecommunications company’s retail stores in the US. Other well-known companies also employ these robots in the US and worldwide:
Our PoC Ransomware
In order to deploy ransomware on these robots an attacker can follow these steps:
- Exploit an undocumented function that allows remote command execution. This vulnerability is being disclosed to the public today. Even though SoftBank was notified January 2017, we aren’t aware of any fix available yet. This undocumented function allows executing commands remotely by instantiating a NAOqi object using the ALLauncher module and calling the internal _launch function.
- Infect *.so module files to change robot default operations, disable administration features, monitor video/audio and send it to a C&C via Internet (e.g.: hooking libmotion.so and libvideo.so)
- Elevate privileges, change SSH settings. Change root password to disable remote access.
- Disrupt factory reset mechanism in order to prevent the user restoring the system or uninstalling the ransomware:
- /etc/init.d/firmware-update
- /usr/libexec/firmware/flash-dspic
- /usr/bin/chest-mode
- /usr/bin/firmware-update
- Notify infection to C&C server
- Infect all behavior files, which contain custom code to execute the main robot business or actions.
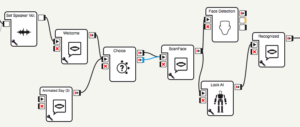
In the following example, a robot greets and listens for orders from customers. Afterwards, the robot does face recognition to detect a customer’s face and give him special discounts or offers.
These .xar behavior files are executed on the robot and are special XML files which contain embedded Python classes. Each box represents one or more classes that get executed. By injecting custom Python code into any of these classes, the robot behavior can be changed in a malicious way without even changing the project file.
The following video shows a proof of concept of the entire ransomware attack:
Possible Ransomware Strategies
- Interrupt service completely – all robots stop working.
- Display adult content (porn) to customers, for instance, on Pepper robot’s tablet whenever the robot is on.
- Curse customers when interacting with them. This impacts differently depending on the country laws or cultural background.
- Perform violent movements in industrial robots at a random time while working.
The Difficulty in Removing Ransomware
As previously mentioned, many robots don’t have an easy and economical way to factory reset when there is a software malfunction. Having a technician fix a robot problem could take weeks depending on availability. Ironically, during our research, our robot started to malfunction. The only option to repair it was to send it back to the vendor. We had to ship it from our country to the US and wait a couple weeks for its return. We also had to cover the associated shipping costs, including customs handling.
Thank you for the information you have provided. We are now going to repair your Robot at Softbank Robotics America, so we would need you to send it to us.
[…]
Please make sure you keep a backup of all your files and behaviors, as we may need to change or update your robot to the latest version of NAO OS / NAOqi.
We look forward to receiving your robot and repairing it as quickly as possible.
Best Regards,
Customer Care
Softbank Robotics America
Next Generation Threats and Conclusions
Businesses lose money every second robots are non-operational – whether through lost revenue, production and/or repair costs. Paying a ransom to quickly get the robots working again could be cheaper than the alternative.