Over the course of a few years and a pandemic, we (AIS and NMFTA) tested several tractor-trailers for the security properties of the trailer databus, J2497 aka PLC4TRUCKS. What we discovered was that 1) this traffic could be read remotely with SDRs and active antennas but, more importantly, 2) that valid J2497 traffic could be induced on the trailer databus using SDRs, power amplifiers and simple antennas. In this blog post we will introduce you to some concepts and the discoveries overall – for the full technical details please get the whitepaper.
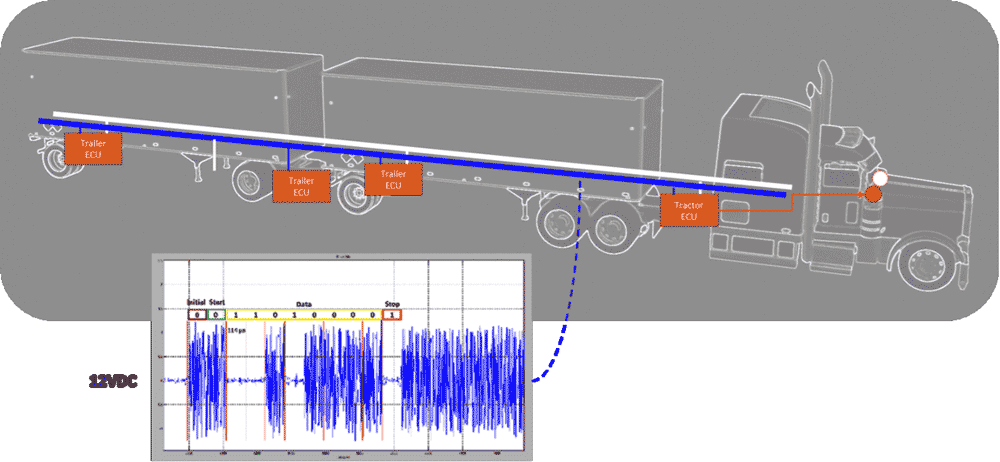
J2497 aka PLC4TRUCKS is a Power Line Carrier (PLC) scheme designed and implemented by Intellon as a bridge between UARTs over powerlines in the Intellon SSC P485 transceiver IC. For years this patented chip was the only way to realize the J2497 standard. With the recent expiration of the patent, this has changed, but the as-implemented behavior of the Intellon chip is still the de facto standard, and the J2497 specification itself has SSC P485-specific components to it. It was developed and deployed as an alternative physical layer to J1708 for the J1587 protocol that sits on top of it; the SSC-P485 converts bi-directionally between J1708 and J2497.
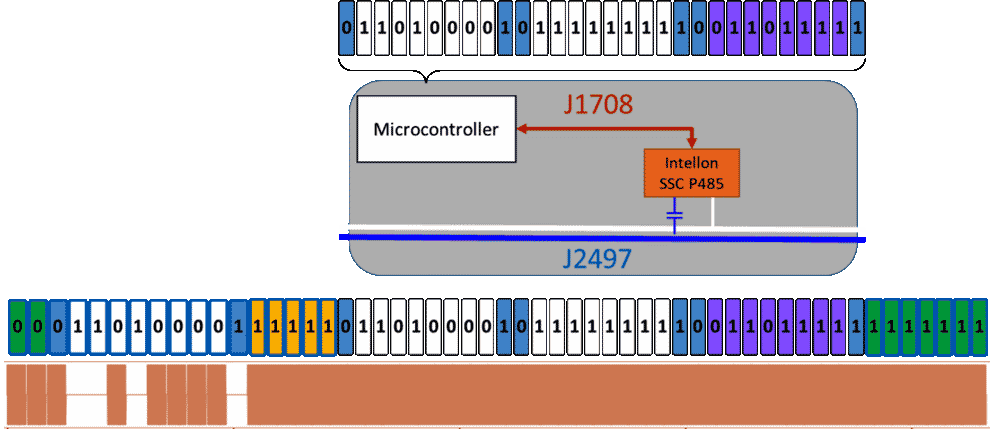
Offering this as a ‘conversion chip’ allowed suppliers to provide PLC4TRUCKS trailer controllers based on previously fielded J1708/J1587 solutions. This was very beneficial for the rapid deployment of solutions for the impending tailer ABS fault lamp regulations of the time but also meant that the trailer equipment inherited legacy features from the J1708/J1587 code. We were very interested in what diagnostic features were implemented in the trailer controllers using J1708/J1587 mechanisms and eventually found during the ‘Powermaster’ project that all trailer controllers and even some tractor controller did respond to the J1708 ‘data link escape’ means of executing proprietary diagnostics.
The ‘Powermaster’ project really kicked off in 2019. Much like the work that Baker, et. al.,[1] released earlier that same year (simultaneous to our own testing, during which we found remote read capability), in which these authors demonstrated that Intellon’s (then-Atheros’, which would become Qualcomm’s) HomePlug GreenPhy (HPGP) Power Line Communications (PLC) can be received at distances of several feet using Software Defined Radios (SDRs). We eventually published our remote read findings at the Car Hacking Village DEF CON 29 SAFE MODE[2] in 2020. Our results were the same: the much earlier (perhaps original) Intellon PLC scheme in J2497 can be read remotely, just like the modern incarnation in HPGP.
The remote read issue was reported in 2020, but during this time we were also testing for remote write – that part didn’t go so smoothly, more on that later. What we eventually confirmed was that it is possible to write remotely to J2497 via induced RF, depending on the equipment configuration (again, just like Baker et. al. who reported a wireless disruption issue in HPGP in February 2022[3]). We found that the most susceptible equipment is tanker trailers and 3x road train trailers. The equipment from all trailer and tractor brake suppliers is affected and the maximum distance can be up to 12 feet. Furthermore, the equipment needed to make it work is not expensive: as cheap as $300 USD for the most susceptible trailer equipment configurations. For details on the confirmed results and testing methods we followed, please consult the tables in NMFTA’s Disclosure of Confirmed Remote Write.[4]
What we’ve confirmed is that all three of today’s trailer brake suppliers implement diagnostics over J1587 on J2497 using Data Link Escapes (DLEs). We have encountered no diagnostics features there that require any authentication or authorization, meaning it is susceptible to a replay attack. In the ‘Powermaster’ project we eventually gravitated to testing with transmission of solenoid test commands because we found we were unable to measure the induced waveform voltages even though the valid J2497 messages were clearly being received; and the solenoid test commands have an audible response from the brake controllers which makes the test tests easy to confirm. It also made it easy to film, which we did and presented a couple videos at our DEF CON 30 talk which is now available on the media server[5].

We still aren’t sure of how the attack to induce valid messages is successful (we do have some theories[6] presented in the whitepaper) but we do know where it works and doesn’t:
- Tankers, which are large metal shells and whose wiring typically runs out along their side, are very susceptible
- Dry vans with wooden decking and metal beams are not very susceptible, as compared to trailers with the same dimensions but with metal decking. In these, the wiring runs under the decking and through the beams. In the metal decking trailers we tested, the wiring ran inside an extruded channel.
- Even the least susceptible dry-van trailers with wooden decking are susceptible when in a 3x road train configuration.
In addition to the Powermaster project with AIS we also developed mitigation techniques and technologies which we released into the public domain[7]. We then worked with CISA VDP on a coordinated disclosure and was able to eventually share the attack and mitigation details with the ATA TMC task forces that are responsible for defining the next generation tract trailer interface and are actively doing so today. The industry is focused on newer communications methods because J2497 never delivered on even its modest bandwidth promises. However, there’s the problem of 20 years’ worth of tractors and trailers using J2497. More than half of them will continue to be used for another 15 years. In addition to requesting that diagnostics on J2497 be excluded from the NGTTI we have also requested that all new tractors include mitigations against the J2497 remote write attack so that new tractors can protect older trailers. And at the Sept 2022 ATA TMC meeting the Task Force accepted our recommendations with a vote of 14 in favor to 4 against.
We will keep working with the ATA TMC task forces to ensure that the next-generation tractor-trailer interface does not inherit the issues we’ve seen in J2497. We are also looking for more testing opportunities to confirm these results on other equipment, as well as opportunities test new concepts.
Don’t forget to access the whitepaper for the full details to the research.
If you would like to host us for some testing[8], please contact ben.gardiner@nmfta.org.
Ben Gardiner
Ben Gardiner is a Senior Cybersecurity Research Engineer contractor presently working to secure commercial transportation at the National Motor Freight Traffic Association (NMFTA). With more than ten years of professional experience in embedded systems design and lifetime worth of hacking experience, he has deep knowledge of the low-level functions of operating systems and the hardware with which they interface. Prior to partnering with the NMFTA team in 2019, he held security assurance and reversing roles at a global corporation, as well as working in embedded software and systems engineering roles at several organizations. He holds a Masters of Science in Engineering in Applied Math & Stats from Queen’s University. He is a DEF CON Hardware Hacking Village (DC HHV) volunteer, is GIAC GPEN certified and a GIAC advisory board member, he is also chair of the SAE TEVEES18A1 Cybersecurity Assurance Testing TF (drafting J3061-2), and a voting member of the SAE Vehicle Electronic Systems Security Committee.
[1] Baker, Richard, and Ivan Martinovic. “Losing the Car Keys: Wireless {PHY-Layer} Insecurity in {EV} Charging.” 28th USENIX Security Symposium (USENIX Security 19), 2019.
[2] Poore, Chris, and Gardiner, Ben. “Power Line Truck Hacking: 2TOOLS4PLC4TRUCKS.” DEF CON 30 Car Hacking Village 2019. http://www.nmfta.org/documents/ctsrp/Power_Line_Truck_Hacking_2TOOLS4PLC4TRUCKS.pdf?v=1
[3] Sebastian Köhler and Richard Baker and Martin Strohmeier and Ivan Martinovic, “Brokenwire : Wireless Disruption of CCS Electric Vehicle Charging” 2022 https://arxiv.org/pdf/2202.02104.pdf
[4] Gardiner, Ben, NMFTA Inc. “2021 Disclosure of Confirmed Remote Write.” http://www.nmfta.org/documents/ctsrp/Disclosure_of_Confirmed_Remote_Write_v4_DIST.pdf?v=1
[5]https://media.defcon.org/DEF%20CON%2030/DEF%20CON%2030%20video%20and%20slides/DEF%20CON%2030%20-%20Ben%20Gardiner%20-%20Trailer%20Shouting%20-%20Talking%20PLC4TRUCKS%20Remotely%20with%20an%20SDR.mp4
[6] the theory that we induce more voltage on the chassis and hence the receiver picks up a single-ended voltage seems promising considering that CharIn has adopted differential PLC for all HPGP connections in their megawatt charging interface
[7] Gardiner, Ben. “Mitigations Options to J2497 Attacks” March 3rd 2022. http://www.nmfta.org/documents/ctsrp/Actionable_Mitigations_Options_v9_DIST.pdf?v=1
[8] Gardiner, Ben. “NFMTA CTSRP Heavy Vehicle Testing Plan” March 1st 2022. https://github.com/nmfta-repo/nmfta-vehicle_cybersecurity_requirements/blob/main/resources/heavy_vehicle_testing_plan.md

