The push to incorporate remote management capabilities into products has swept across a number of industries. A good example of this is the famous Internet of Things (IoT), where modern home devices from crockpots to thermostats can be managed remotely from a tablet or smartphone.
One of the biggest problems associated with this new feature is a lack of security. Unfortunately, nobody is surprised when a new, widespread vulnerability appears in the IoT world.
However, the situation becomes a bit more concerning when similar technologies appear in the aviation sector. Nowadays we can find Cabin Management and In-Flight entertainment systems that can be managed from mobile devices owned by crew members and/or passengers.
The systems I’ve analyzed in the research presented here, are deployed in business jets. The discovered vulnerabilities affect passenger and crew devices.
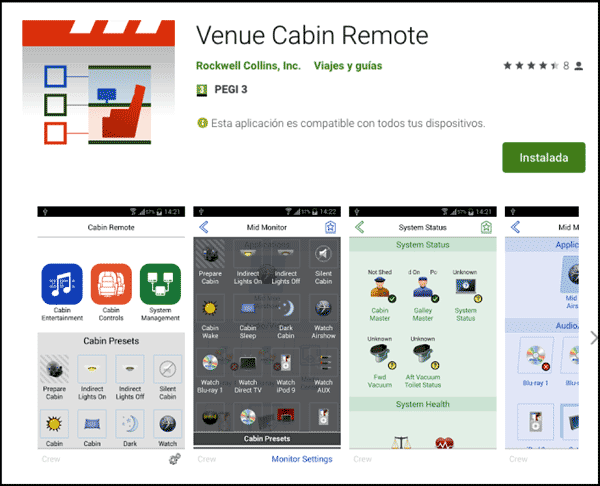
The Cabin Management System is based on a wireless access point installed onboard the aircraft that provides network connectivity from the mobile devices of passengers and crew members to the cabin server. The Android applications (and their iOS equivalents) for both vendors were developed by Rockwell Collins to manage the available cabin capabilities in the aircraft such as cabin temperature, light intensity and much more.
Manufacturer video promo: https://www.youtube.com/watch?v=pRA3AnPU1dE
The Android apps analyzed in this post are:
- Venue Cabin Remote by Rockwell Collins – Android Application Version 2.1.12 (Current Version 2.2.2) (https://play.google.com/store/apps/details?id=com.rockwellcollins.venue.cabinremote)
- Bombardier Cabin Control – Android Application Version 2.1.12 (Current Version 2.2.1) (https://play.google.com/store/apps/details?id=com.rockwellcollins.venue.cabinremote.bombardier)

The purpose of this post is to:
- Provide an overview of the operations of these emergent systems, with a focus on the vulnerabilities that affect the Android mobile apps
- Provide a detailed explanation on how to exploit them
The main vulnerabilities I’ve discovered in the systems are:
- ZIP Files: Path traversal / Arbitrary File Write
- Rockwell Collins Venue Cabin Remote Version 2.1.12 – Arbitrary Write File https://youtu.be/OkvfwEBFiWY
- Bombardier Cabin Control Version 2.2.1 (Last version 1st April) – Arbitrary File Write in SDcard https://youtu.be/_3cqNwwiF9k
- Lack of Legitimacy Checking of the Server
- Rockwell Collins Venue Cabin Remote Version 2.2.2 – Legit Connectivity AP Emulation https://youtu.be/8QRAlTBOatU
- Unencrypted Communications
Based on the vulnerabilities found during the research, an attacker could create the following situations:
- Deploy a rogue aircraft access point and write in the devices of the connected clients. This could lead to a full compromise of the device.
- Deploy a rogue aircraft access point and capture credentials or application secrets used to get access to protected areas in the application managed by the crew members in the real aircraft access point.
- Connect to a real aircraft access point and interact with the cabin devices using the application. This could lead to full access to the cabin capabilities via the application if the attacker gets the password to access protected application menus and create situations of discomfort onboard an aircraft by altering the temperature to a higher or lower value or modifying light intensity, switching off or blinking.
- Connect to a real aircraft access point and multicast other server configuration to force the devices that are connected to the network to get a new configuration file, this could lead to some dangerous situations like:
- A full compromise of the client’s devices connected to the network.
- Create situations of discomfort onboard an aircraft by altering the temperature to a higher or lower value or modifying light intensity, switching off or blinking.
Research Timeline:
- 2018 February: IOActive discovers vulnerability
- 2018 February: IOActive notifies vendor
- 2019 April: IOActive advisory published
Dani Martinez – @dan1t0 (https://twitter.com/dan1t0)
Security Consultant
The complete research, including: full systems overview and analysis, vulnerability discoveries with the Android apps, and detailed exploit scenarios, can be found on the Technical Advisory Paper.

