The maritime sector makes use of some of these systems to track and monitor ships’ IT and navigation systems as well as to aid crew members in some of their daily duties, providing them with e-mail or the ability to browse the Internet. Modern vessels don’t differ that much from your typical office these days, aside from the fact that they might be floating in a remote location.
Satellite connectivity is an expensive resource. In order to minimize its cost, several products exist to perform optimizations around the compression of data while in transit. One of the products that caught our eye was AmosConnect.
AmosConnect 8 is a platform designed to work in a maritime environment in conjunction with satellite equipment, providing services such as:
- E-mail
- Instant messaging
- Position reporting
- Crew Internet
- Automatic file transfer
- Application integration
We have identified two critical vulnerabilities in this software that allow pre-authenticated attackers to fully compromise an AmosConnect server. We have reported these vulnerabilities but there is no fix for them, as Inmarsat has discontinued AmosConnect 8, announcing its end-of-life in June 2017. The original advisory is available here, and this blog post will also discuss some of the technical details.
Blind SQL Injection in Login Form
A Blind SQL Injection vulnerability is present in the login form, allowing unauthenticated attackers to gain access to credentials stored in its internal database. The server stores usernames and passwords in plaintext, making this vulnerability trivial to exploit.
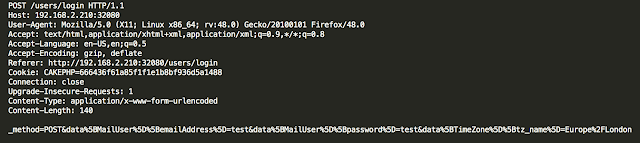
The following POST request is sent when a user tries to log into AmosConnect
The parameter data[MailUser][emailAddress] is vulnerable to Blind SQL Injection, enabling data retrieval from the backend SQLite database using time-based attacks.
Attackers that successfully exploit this vulnerability can retrieve credentials to log into the service by executing the following queries:
SELECT key, value from MOBILE_PROPS WHERE key LIKE ‘USER.%.password’;
SELECT key, value from MOBILE_PROPS WHERE key LIKE
‘USER.%.email_address’;
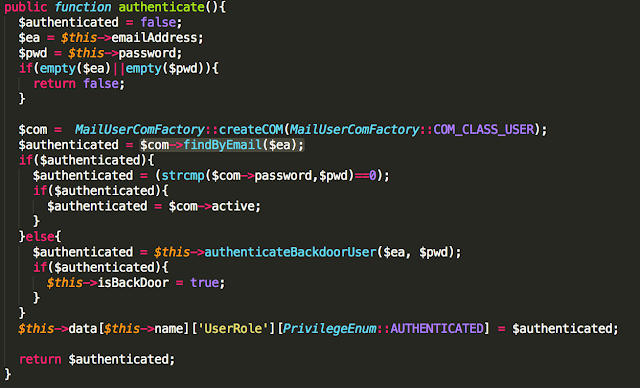
The authentication method is implemented in mail_user.php:
The call to findByEmail() instantiates a COM object that is implemented in native C++ code.
The following C++ native methods are invoked upon execution of the call:
Neptune::UserManager::User::findByEmai(…)
Neptune::ConfigManager::Property::findBy( … )
Neptune::ConfigManager::Property::findAllBy( … )
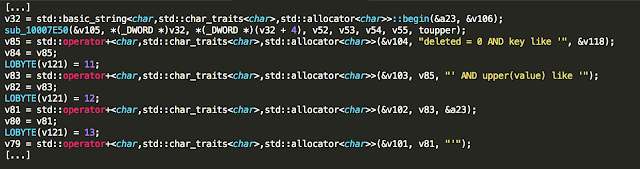
The vulnerable code is implemented in Neptune::ConfigManager::Property::findAllBy() as seen below:
Strings are concatenated in an insecure manner, building a SQL query that in this case would look like:
“[…] deleted = 0 AND key like ‘USER.%.email_address’ AND upper(value) like ‘{email}'”
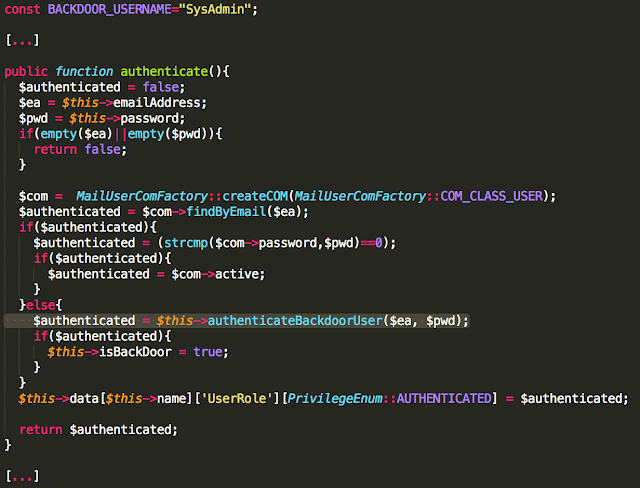
Privileged Backdoor Account
The AmosConnect server features a built-in backdoor account with full system privileges. Among other things, this vulnerability allows attackers to execute commands with SYSTEM privileges on the remote system by abusing AmosConnect Task Manager.
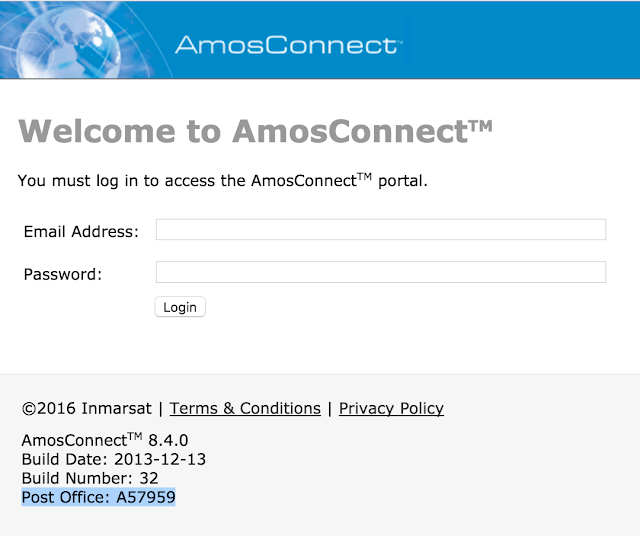
Users accessing the AmosConnect server see the following login screen:
The login website reveals the Post Office ID, this ID identifies the AmosConnect server and is tied to the software license.
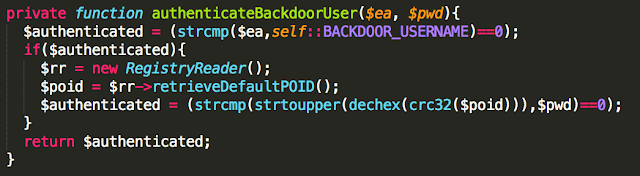
The following code belongs to the authentication method implemented in mail_user.php. Note the call to authenticateBackdoorUser():
authenticateBackdoorUser() is implemented as follows:
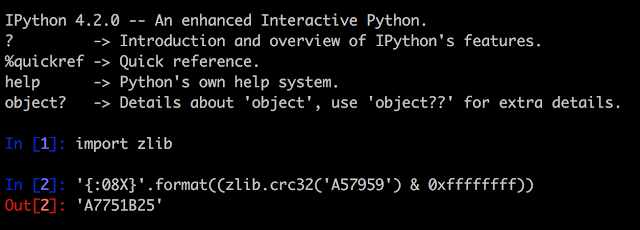
The following code snippet shows how an attacker can obtain the SysAdmin password for a given Post Office ID:
Conclusions and thoughts
Vessel networks are typically segmented and isolated from each other, in part for security reasons. A typical vessel network configuration might feature some of the following subnets:
· Navigation systems network. Some of the most recent vessels feature “sail-by-wire” technologies; the systems in charge of providing this technology are located in this network.
· Industrial Control Systems (ICS) network. Vessels contain a lot of industrial machinery that can be remotely monitored and operated. Some vessels feature a dedicated network for these systems; in some configuration, the ICS and Navigation networks may actually be the same.
· IT systems network. Vessels typically feature a separate network to support office applications. IT servers and crew members’ work computers are connected to this network; it’s within this network that AmosConnect is typically deployed.
· Bring-Your-Own-Device networks. Vessels may feature a separate network to provide internet connectivity to guests or crew members’ personal devices.
· SATCOM. While this may change from vessel to vessel, some use a separate subnet to host satellite communications equipment.
While the vulnerabilities discussed in this blog post may only be exploited by an attacker with access to the IT systems network, it’s important to note that within certain vessel configurations some networks might not be segmented, or AmosConnect might be exposed to one or more of these networks. A typical scenario would make AmosConnect available to both the BYOD “guest” and IT networks; one can easily see how these vulnerabilities could be exploited by a local attacker to pivot from the guest network to the IT network. Also, some the vulnerabilities uncovered during our SATCOM research might enable attackers to access these systems via the satellite link.
All in all, these vulnerabilities pose a serious security risk. Attackers might be able to obtain corporate data, take over the server to mount further attacks or pivot within the vessel networks.
References:
https://shiptracker.shodan.io/