People are always on the move, changing their homes and their workspaces. With increasing frequency, they move from their current jobs to new positions, seeking new challenges, new people and places, to higher salaries.
Time and hard work bring experience and expertise, and these two qualities are what companies look for; they’re looking for skilled workers every single day, on multiple job search and recruiting platforms. However, these job postings might reveal sensitive information about the company that even the most seasoned Human Resources specialists don’t notice.
Job posting websites are a goldmine of information. Inherently, recruiters have to disclose certain data points, such as the technologies used by the company, so that candidates can assess whether they should apply. On the other hand, these data points could be used by malicious actors to profile a specific company and launch more sophisticated targeted attacks against the company and its employees.
To demonstrate this concept, I did research on tens of job postings from the following websites:
- LinkedIn – https://www.linkedin.com/jobs/
- Glassdoor – https://www.glassdoor.com
- Indeed – https://www.indeed.com
- CareerBuilder – https://www.careerbuilder.com
- Monster – https://www.monster.com
- ZipRecruiter – https://www.ziprecruiter.com
- Ladders – https://www.theladders.com
- Wellfound – https://wellfound.com
Surprisingly, more than 40% of job postings reveal relatively sensitive information, such as the following, which are just a sample of the information obtained from a variety of companies:
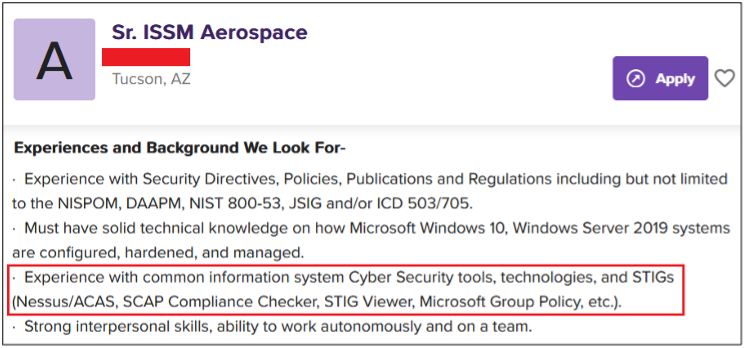
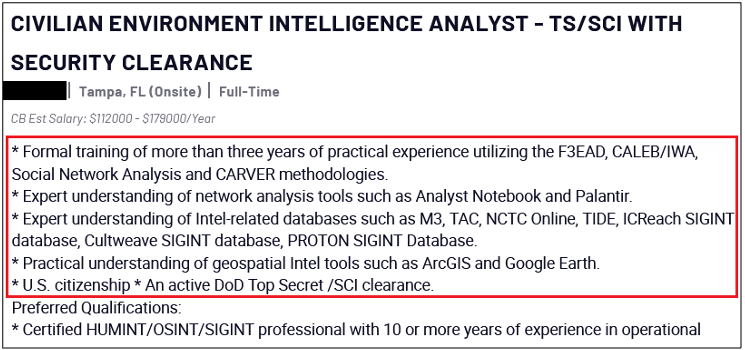
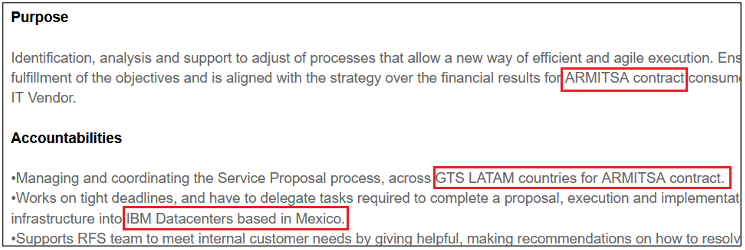

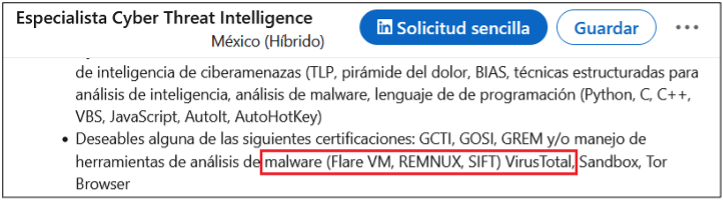
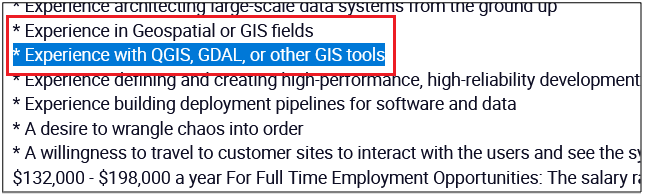
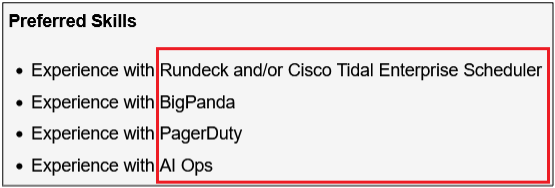
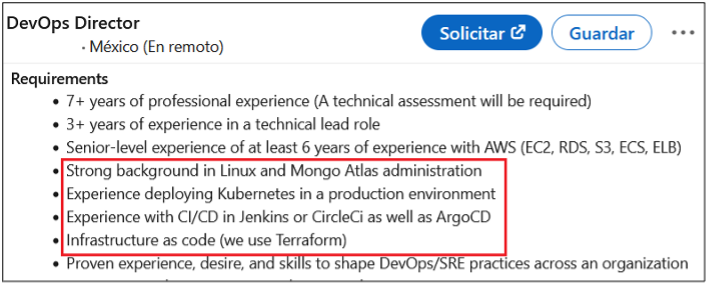
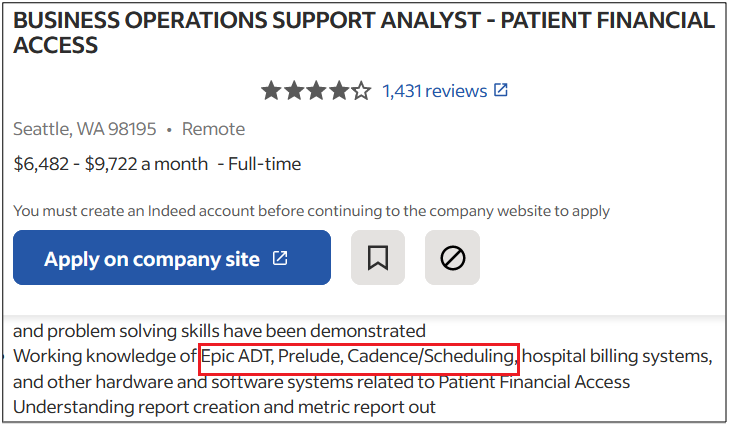
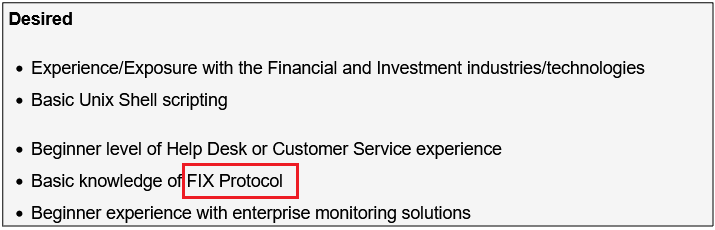
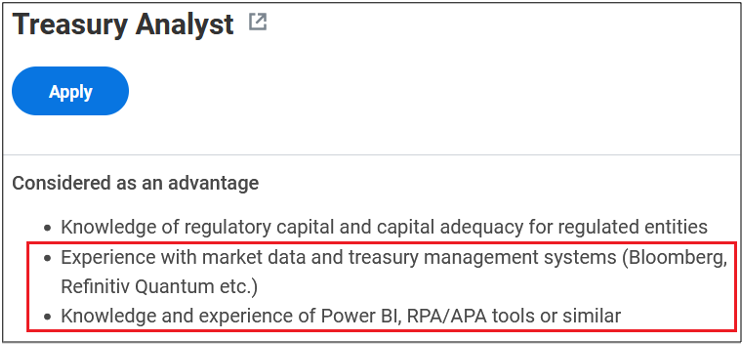
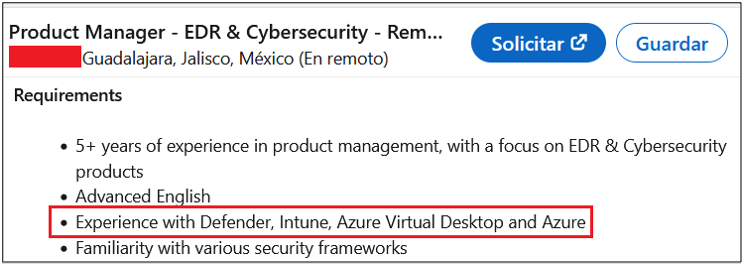
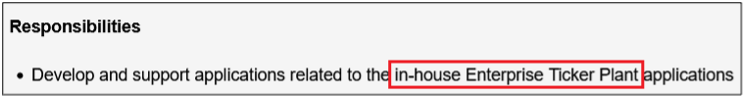
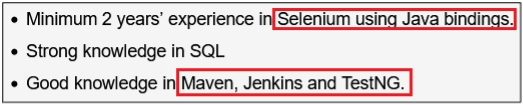

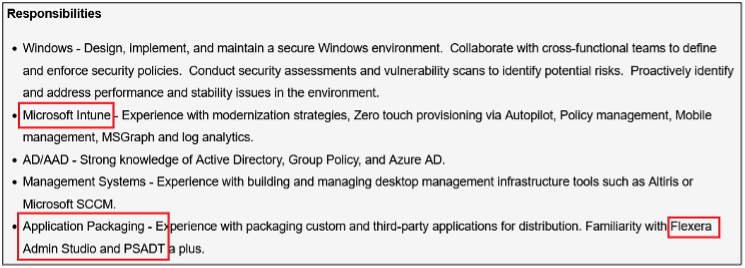
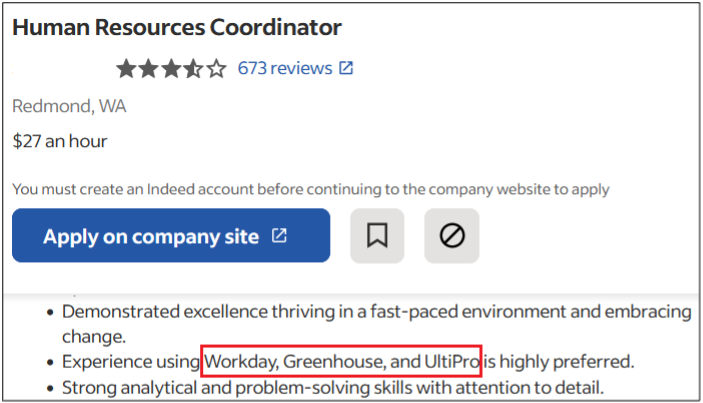
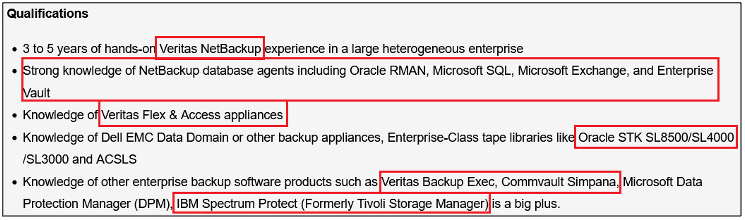
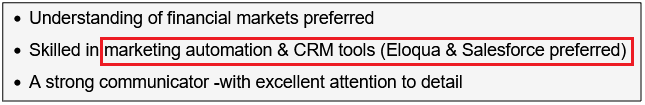
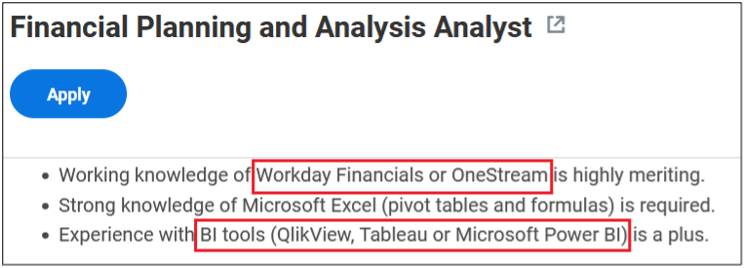
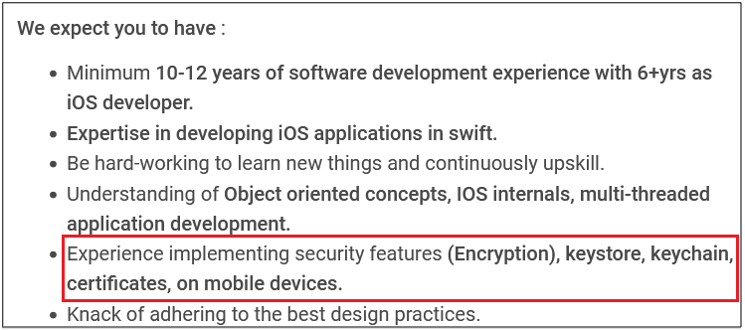
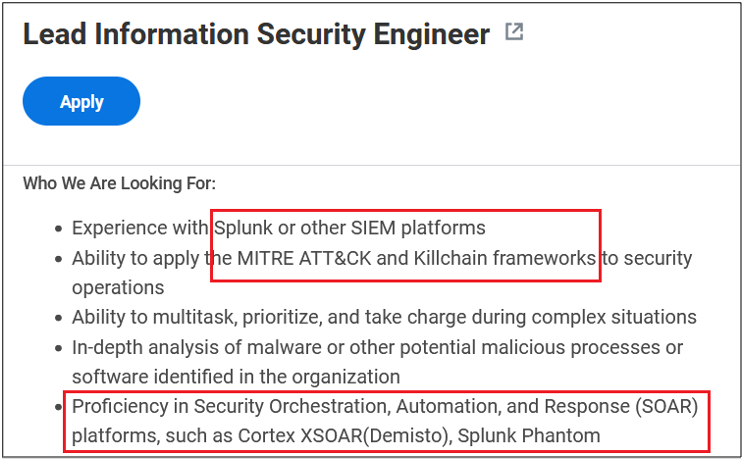
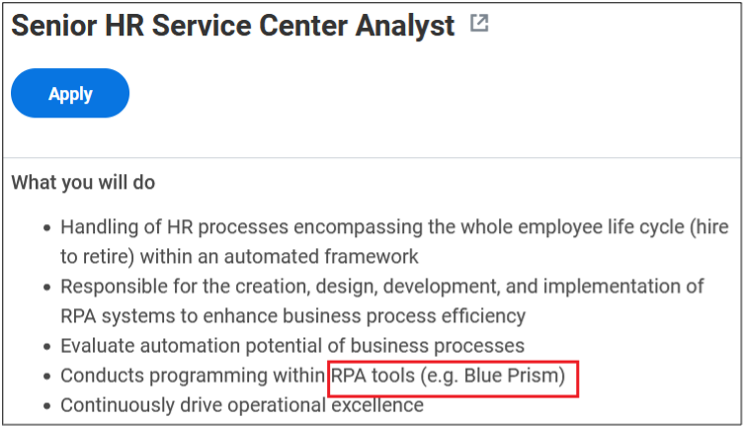
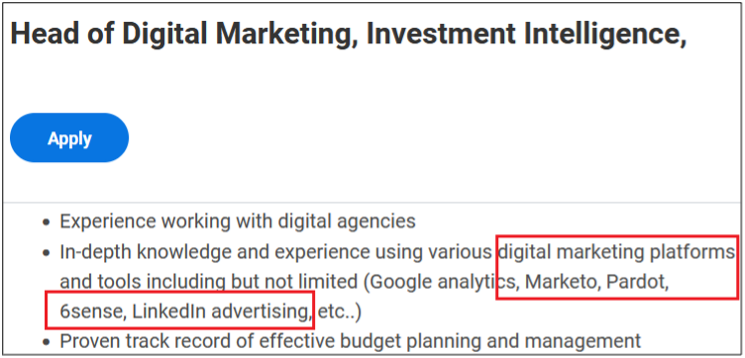
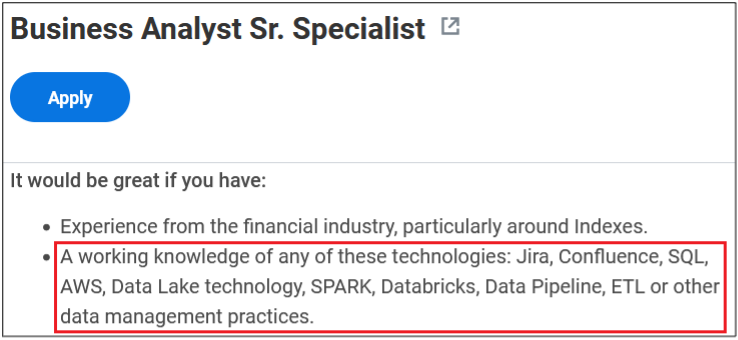
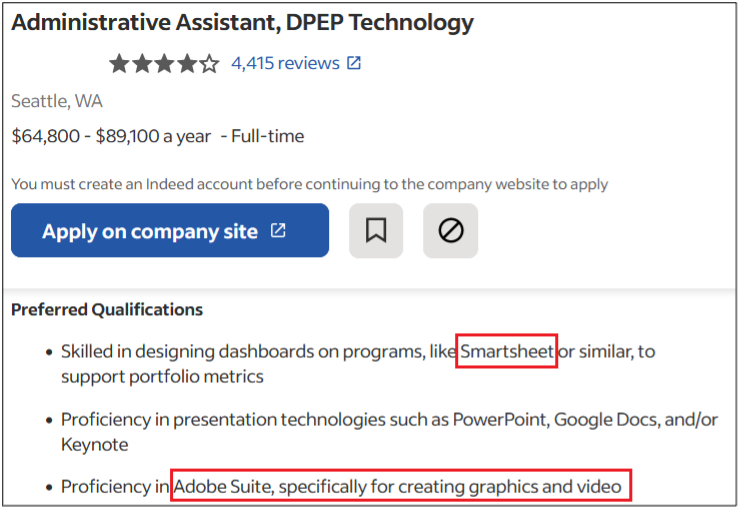
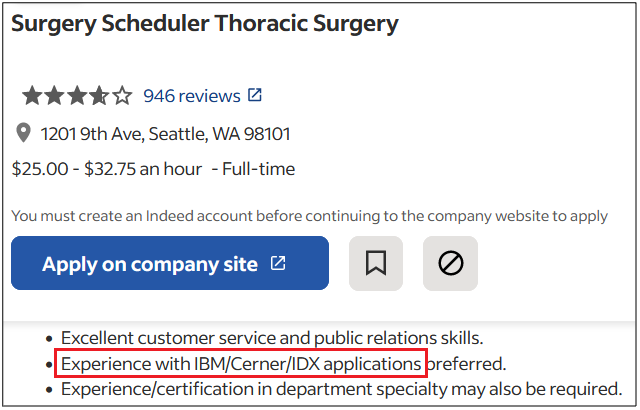
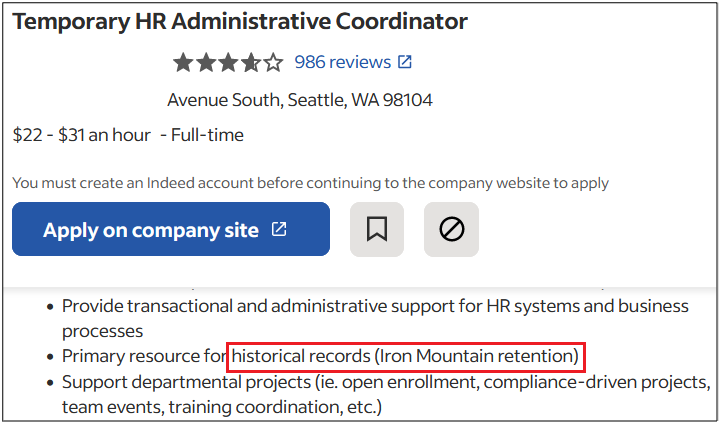
As you can see, a variety of information is disclosed inadvertently in these job postings:
- Exact version of the software used in the backend or by end users
- Programming languages, frameworks and libraries used
- Cloud Service Providers where customer data resides
- Intranet and collaborative software used within the company
- Antivirus and endpoint security software in use
- Industry-specific and third-party software used
- Databases, storage and backup, and recovery platforms used
- Business relationships with other companies
- Security controls implemented in the company’s SDLC
Armed with this information, one can simply connect the data dots and infer things like:
- Whether a company uses proprietary or open-source software, implying the use of other similar proprietary/open-source applications that could be targeted in an attack.
- Whether a company performs Threat Modeling and follows a secure SDCL, providing an attacker with a vague idea of whether the in-house-developed applications are secure or not.
- Whether a company has business relationship with other companies, enabling an attacker to target third-party companies in order to use them as pivot to attack the targeted company.
In summary, IOActive strongly encourages recruiters not to include sensitive information other than that required by the job position – in attempting to precisely target the exact candidate for a job, the level of detail you use could be costly.

