Everything is ‘Connected’ in Today’s Modern Airports
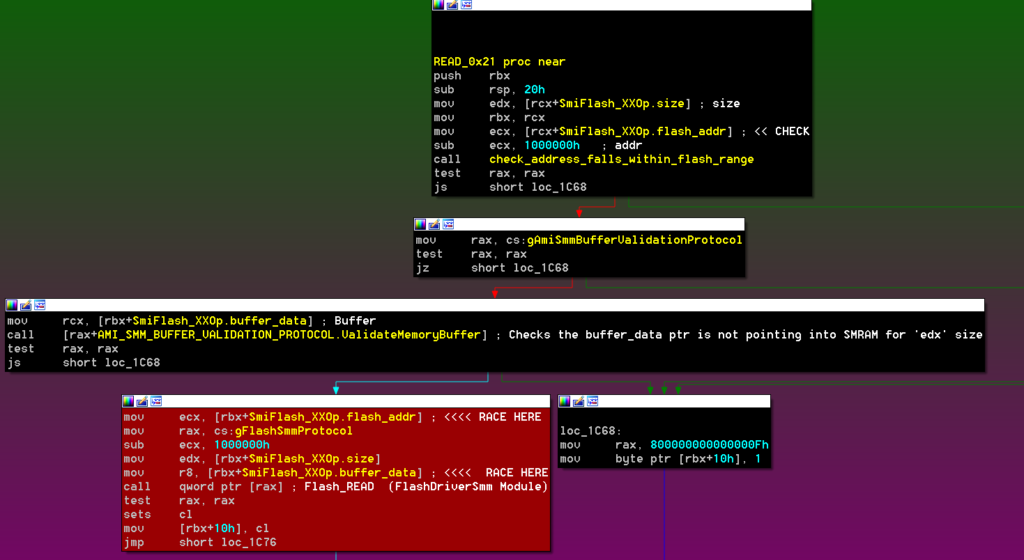
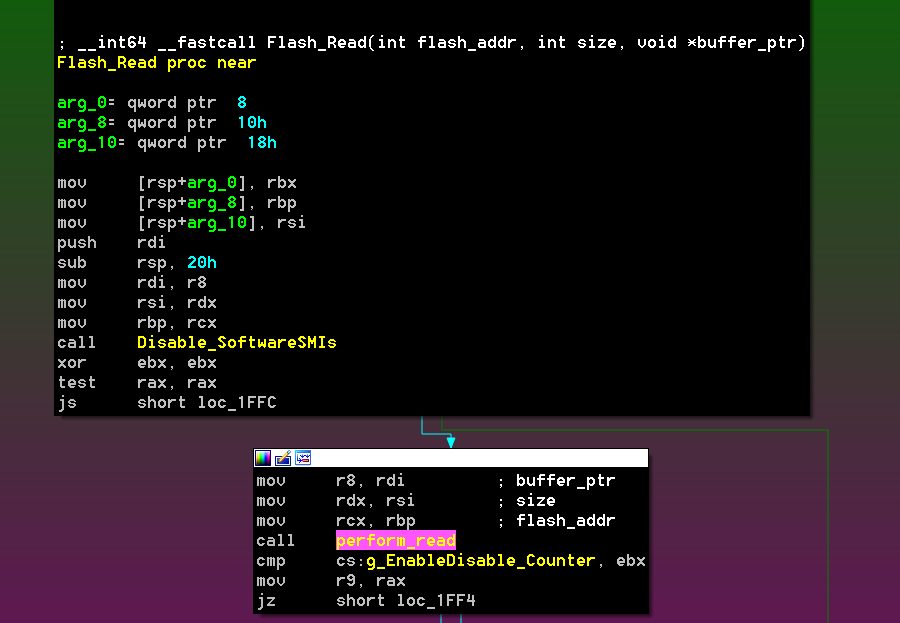
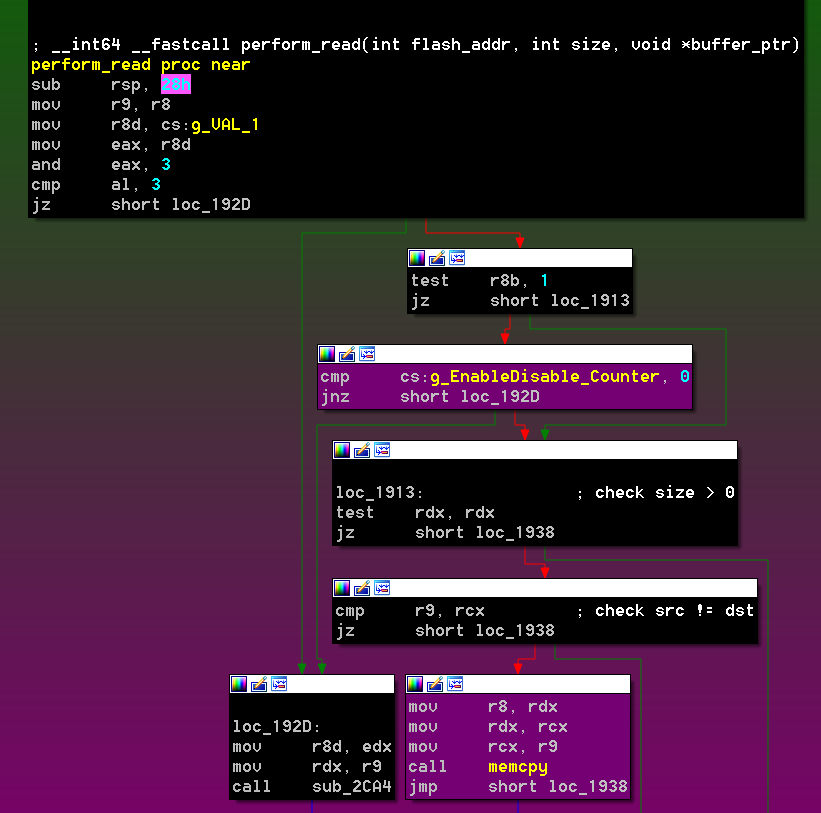
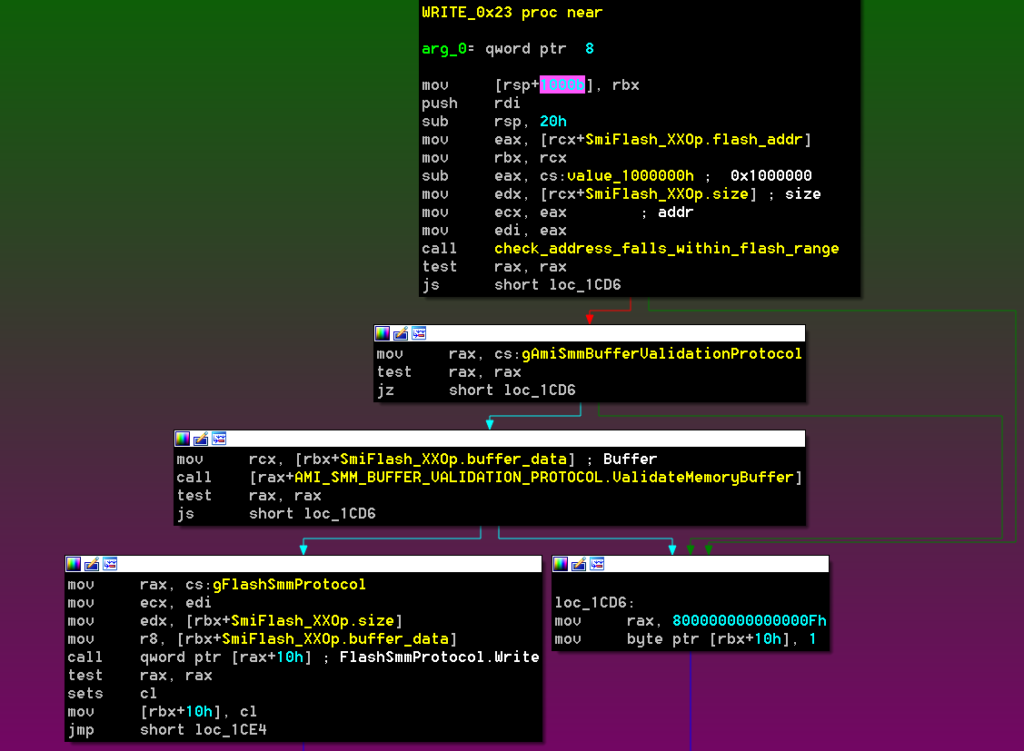
Cybersecurity in global aviation is increasingly dependent on vulnerabilities in Information Technology (IT) and Operational Technology (OT) systems. The definition of OT systems in this context is defined as hardware and software dedicated to detecting or causing changes in physical processes through direct monitoring and/or control of physical devices such as valves or pumps. OT systems are much less organized and are rarely monitored as closely as conventional IT networks. Airports use several critical OT systems, including baggage handling, airport refueling systems, runway lights, building management systems, and supervisory control and data acquisition systems (SCADA)/industrial control systems (ICS).
At most modern airports, there are many cyber-physical security (CPS) challenges to be met, and airport CPS systems fall into three broad categories, each managed by means of network-connected digital controllers:
- OT Systems – baggage handling systems, building management systems (mechanical, HVAC, electrical systems, lighting, alarms, and sensors), SCADA/ICS, airport refueling/SCADA systems, Approach Lighting System (ALS), Instrument Landing Systems (ILS), electronic baggage tags, etc.
- IT Systems – video security surveillance systems, access control/badging, contactless mobile payment systems, barcode systems, license readers/parking lots, etc.
- Ground Vehicles – de-icing trucks, Aircraft Rescue and Firefighting (ARFF) trucks, heavy-duty electric trucks, Electric Vehicle Supply Equipment (EVSE) chargers, snowplow trucks, remote-control airport tugs, Automotive People Movers (APM), Automated Guideway Transit (AGT), Personal Rapid Transit (PRT), automated shuttles, autonomous vehicles, etc.
Today’s Cybersecurity Threats at Airports is Increasing Exponentially
Persistent cybersecurity threats against the aviation sector pose a danger to world airport travel and safety, including unidentified malicious cyber actors who have specifically targeted the U.S. aviation sector over the past few years. Aviation entities have frequently reported incidents such as increased interactions with known malicious foreign IP addresses, phishing emails impersonating legitimate companies, brute-force attacks, and attempts to install backdoors on victim networks.
This accumulation of incidents, which include the following recent examples, underscores the ongoing threat to the aviation sector and the unacceptable risks associated with delay or inaction:
| Date(s) | Incident |
| May 2021 | Society International Telecommunication for Aeronautics (SITA), a telecommunications and IT provider used by approximately 90% of airlines, was the target of a cyberattack, in which threat actors stole over two million records. Affected entities included Air India, Singapore Airlines, Thai Airways, Finnair, Cathay Pacific, United, Air New Zealand, and others. |
| September 2022 | An unidentified cyber actor conducted a brute force cyberattack targeting an identified US airline. This cyberattack originated from Russian IP space and caused airline employees to be locked out of their accounts. |
| October 2022 | US airport websites suffered a cyberattack, and pro-Russian hacking groups listed multiple U.S. airports as targets. |
| October 2022 | A pro-Russian criminal group named KillNet claimed to be behind a significant distributed denial of service (DDoS) attack that impacted several major airports in the United States. DDoS attacks can cripple online services and affect their availability to consumers if the company running those services doesn’t take the appropriate precautions. The group that claimed responsibility for this latest attack carried out similar attacks in the past six months in Europe. The websites of numerous airports were affected, including Atlanta, Los Angeles, Chicago, Orlando, and Phoenix. |
| October 2022 | FireEye has reportedly observed at least 24 different advanced threat actor groups targeting various aspects of the aviation and aerospace industries. These include aerospace and defense parts wholesalers, aerospace products and parts manufacturing, aircraft engine and parts manufacturing, guided missile and space vehicle manufacturing, and industrial and military computer system manufacturing. The majority of these groups were Chinese nexus state-sponsored threat actor groups. |
| May 2023 | Personal information was compromised in a breach at third-party vendor pilotcredentials.com, including name and social security number, driver’s license number, passport number, date of birth, Airman Certificate number, and other government-issued identification numbers, according to breach notifications from the airlines. |
| September 2023 | State-sponsored threat actors have exploited a US aeronautical organization, using known vulnerabilities in Zoho ManageEngine software and in Fortinet firewalls. The organization has not been named, but a statement by US Cyber Command said the attack illuminated “Iranian exploitation efforts. it also said the organization was under attack by “multiple nation-states.” |
In a September 2022 article titled “Top Cyber Threats Faced by the Aviation Industry,” SOCRadar reported that the aviation industry faces a landscape of cyber threats that has constantly evolved and posed new challenges for airports and airlines. The article noted that airport websites across the country were the target of Distributed Denial-of-Service (DDoS) attacks last year that temporarily shut down access to several sites, while ransomware attacks and data breaches remained a majority of incidents impacting the industry since 2020.
In recent years, cyber incidents in the aviation industry have been reviewed within the context of events monitored by Eurocontrol, a pan-European, civil-military organization dedicated to supporting European aviation, who publish the EATM-CERT (European Air Traffic Management Computer Emergency Response Team) Aviation Cyber Event Map. The data in this map has led to the following findings:
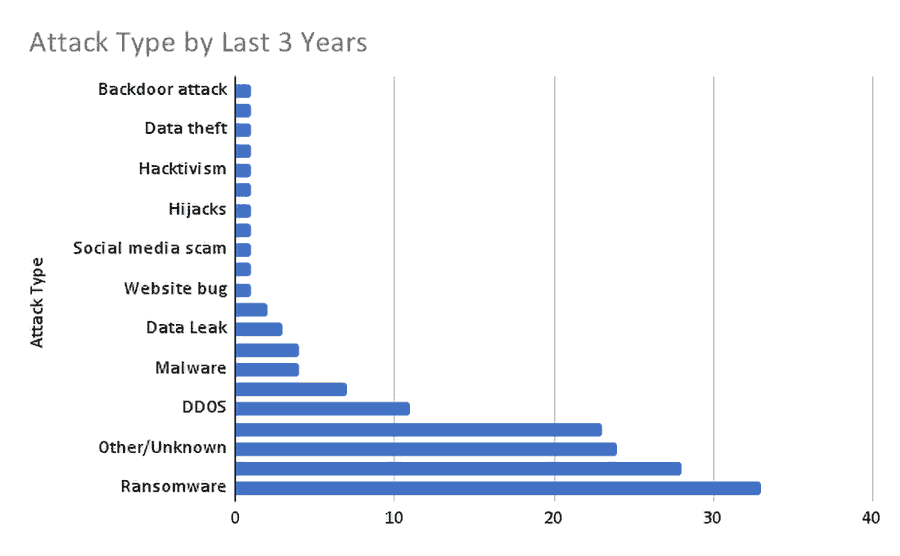
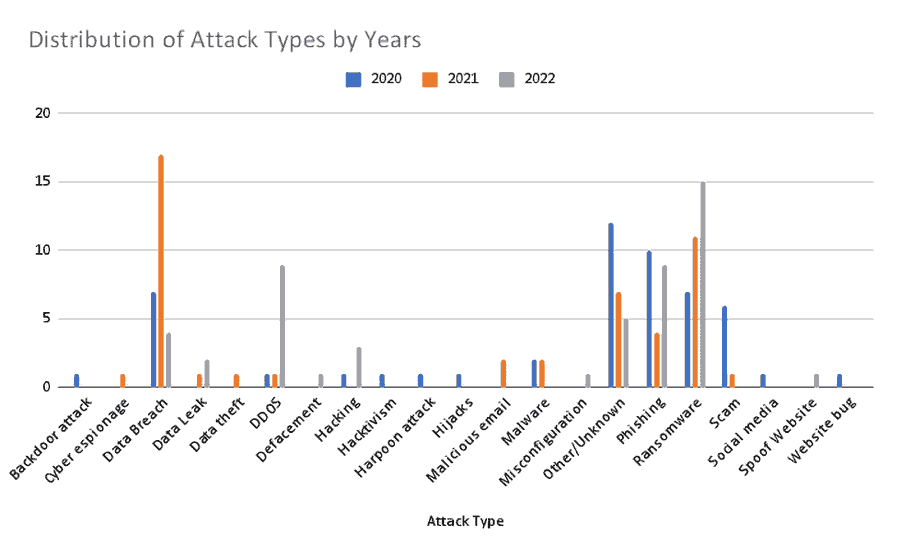
- 52 attacks were reported in 2020, and 48 attacks were reported in 2021. 50 attacks were reported through the end of August 2022, with cyber incidents reaching the previous years’ totals in just eight months.
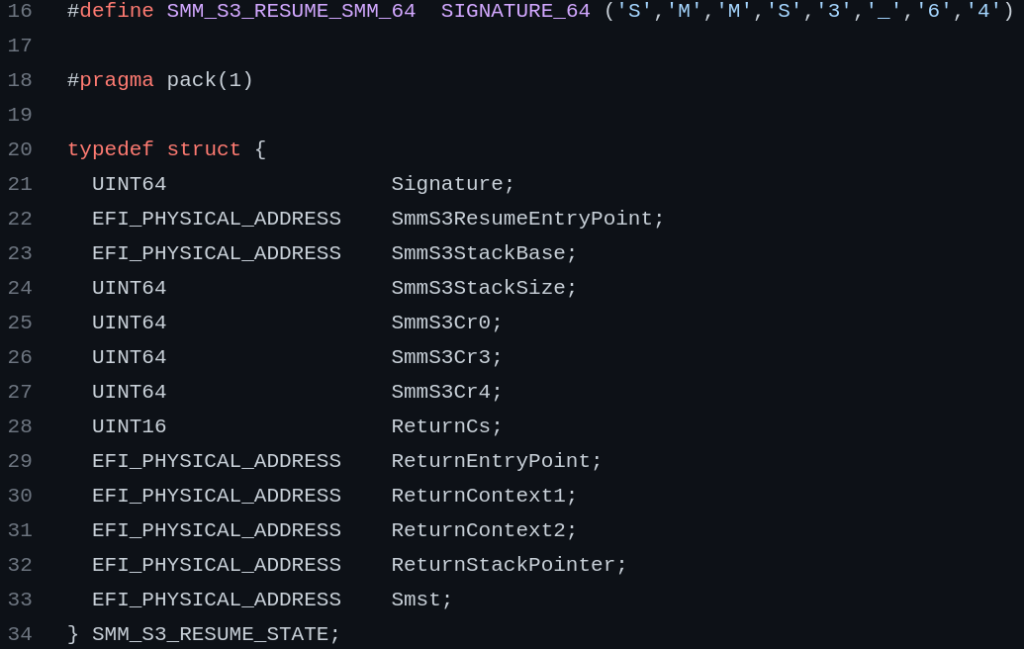
- The most seen attack types in the last three years (2020, 2021, and 2022) are ransomware (%22), data breaches (%18.6), phishing (%15.3), and DDoS (%7.3).
- In addition to civil aviation attacks, eight military-related incidents were reported, with some focused on cyber espionage and data theft. Two of these attacks were carried out with ransomware, two with malware, and one with a backdoor.
Attack types targeting the aviation industry and their distribution are enumerated in the following diagrams.
TSA’s New Cybersecurity Requirements Regulation for Airport and Aircraft Operators
The TSA has taken emergency action in response to the increased threats and vulnerabilities at airports and airlines, issuing a Joint Emergency Amendment (EA) 23-01 Cybersecurity – Performance-Based Measures on March 7, 2023 for all world-wide Category I and II airports.
In summary, the EA 23-01 requirements include:
- Designate Critical Systems (e.g., baggage handling systems, airport re-fueling systems) and submit certain identifying information to TSA
- Develop and implement a Cybersecurity Implementation Plan (CIP) for TSA approval that demonstrates how the regulated entity applies or will apply four performance-based cybersecurity measures to each designated Critical System:
- Network Segmentation – Develop network segmentation policies and controls to ensure that operational technology systems can continue to safely operate in the event that an information technology system has been compromised, and vice versa
- Access Control – Create access control measures to secure and prevent unauthorized access to critical cyber systems
- Continuous Monitoring and Detection – Implement continuous monitoring and detection policies and procedures to defend against, detect, and respond to cybersecurity threats and anomalies that affect critical cyber system operations
- Vulnerability Patching – Reduce the risk of exploitation of unpatched systems through the application of security patches and updates for operating systems, applications, driver and firmware on critical cyber systems in a timely manner using a risk-based methodology.
- Develop and implement an annual Cybersecurity Assessment Program (CAP) that proactively assesses Critical Systems to ascertain the effectiveness of cybersecurity.
For the purposes of this EA, TSA defines a Critical System as any IT or OT system used by the airport or aircraft operator that, if compromised or exploited, could result in operational disruption incurred by the airport or aircraft operator.
IOActive provides services for customers that would assist in meeting the EA 23-01 cybersecurity requirements, such as penetration testing (white-box, gray-box, or black-box), vulnerability assessments, red/purple teams, vulnerability scanning, asset inventory verification, reverse engineering, code reviews, and cybersecurity architecture reviews.
Conducting Cybersecurity Assessments at Airports
Normally when we think of Airport Security we’re thinking about the physical aspects. Everyone has gone through the body scanners, metal detectors, taken their shoes off, opened their bags for a search, accidentally packed 4oz. of toothpaste, etc. However, when examining the cybersecurity ecosystem of an airport there is also a lot to learn about that particular environment.
- Vulnerability Assessments: Instead of just a traditional scan of a website, when doing a full vulnerability assessment of an airport, we can learn a lot about asset management and how the digital attack surface is shaping up and changing over time.
- Red Teaming: Really thinking outside of the box of how a set of attackers can breach an airport in various ways is important to understand where they are weak. From SCADA systems to bag management applications, airports provide a very unique set of challenges for a modern red team.
- Purple Teaming: A proper feedback loop between red team findings and a team responsible for defending the airport is critical to make sure it is not just another PDF report of findings that don’t get addressed. Enabling threat hunting with meaningful data purpose fit for airports is invaluable for teams with this unique set of challenges.
Over the past few years, IOActive has conducted extensive cybersecurity engagements at critical world-wide airports, such as:
- European Airport: IOActive penetration-tested “representative” baggage handling and building management systems, as well as an Industrial Control System (ICS) security monitoring system and created a Test Specification to test the “Live” equipment
- US Airport: IOActive conducted a Security Architecture review of a major SCADA system before it was installed and major vulnerabilities were found in the remote maintenance devices.
- US Airport: IOActive using the Department of Homeland Security (DHS) Cybersecurity Evaluation Tool (CSET), conducted a risk assessment on baggage handling systems and vulnerabilities were found in the technician’s authentication to the equipment
- US Airport: IOActive assisted the airport to develop a Cybersecurity Implementation Program (CIP) and Cybersecurity Assessment Program (CAP) to meet the new TSA-approved Security Program regulations for airports and aircraft operators . A credentialing system, secure remote access and auditing/logging capabilities were implemented to mitigate vulnerabilities found in the Industrial Control System (ICS)/OT Segmentation (e.g. Access Control, Fuel Distribution, Baggage Handling, HVAC, and CCTV systems)
IOActive has seen many systems during our other engagements that have threatscape overlaps with airports. From SCADA/ICS systems to Programmable Logic Controllers (PLCs), pipelines, and even gas turbines. We’ve assessed electricity generation/transmission/distribution systems and even power plants, which all have applicable similarities to airports from a cybersecurity risk point of view.
Kevin Harnett is a Senior Transportation Cybersecurity Technical Advisor for IOActive with deep expertise and experience in ground vehicle and aviation/airport cybersecurity. Kevin has over 40 years experience with the Department of Transportation’s (DOT) Volpe Center.