Year: 2015
Maritime Security: Hacking into a Voyage Data Recorder (VDR)
There are multiple facilities, devices, and systems located on ports and vessels and in the maritime domain in general, which are crucial to maintaining safe and secure operations across multiple sectors and nations.
This blog post describes IOActive’s research related to one type of equipment usually present in vessels, Voyage Data Recorders (VDRs). In order to understand a little bit more about these devices, I’ll detail some of the internals and vulnerabilities found in one of these devices, the Furuno VR-3000.
(http://www.imo.org/en/OurWork/Safety/Navigation/Pages/VDR.aspx ) A VDR is equivalent to an aircraft’s ‘BlackBox’. These devices record crucial data, such as radar images, position, speed, audio in the bridge, etc. This data can be used to understand the root cause of an accident.
Several years ago, piracy acts were on the rise. Multiple cases were reported almost every day. As a result, nation-states along with fishing and shipping companies decided to protect their fleet, either by sending in the military or hiring private physical security companies.
Curiously, Furuno was the manufacturer of the VDR that was corrupted in this incident. This Kerala High Court’s document covers this fact: http://indiankanoon.org/doc/187144571/ However, we cannot say whether the model Enrica Lexie was equipped with was the VR-3000. Just as a side note, the vessel was built in 2008 and the Furuno VR-3000 was apparently released in 2007.
During that process, an interesting detail was reported in several Indian newspapers.
http://www.thehindu.com/news/national/tamil-nadu/voyage-data-recorder-of-prabhu-daya-may-have-been-tampered-with/article2982183.ece
From a security perspective, it seems clear VDRs pose a really interesting target. If you either want to spy on a vessel’s activities or destroy sensitive data that may put your crew in a difficult position, VDRs are the key.
Understanding a VDR’s internals can provide authorities, or third-parties, with valuable information when performing forensics investigations. However, the ability to precisely alter data can also enable anti-forensics attacks, as described in the real incident previously mentioned.
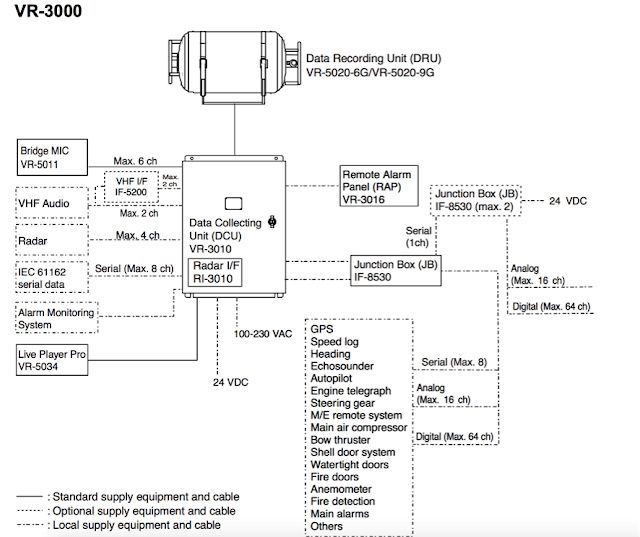
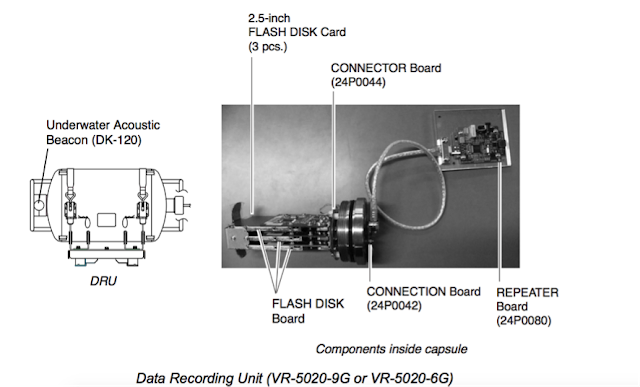
Basically, inside the Data Collecting Unit (DCU) is a Linux machine with multiple communication interfaces, such as USB, IEEE1394, and LAN. Also inside the DCU, is a backup HDD that partially replicates the data stored on the Data Recording Unit (DRU). The DRU is protected against aggressions in order to survive in the case of an accident. It also contains a Flash disk to store data for a 12 hour period. This unit stores all essential navigation and status data such bridge conversations, VHF communications, and radar images.
The International Maritime Organization (IMO) recommends that all VDR and S-VDR systems installed on or after 1 July 2006 be supplied with an accessible means for extracting the stored data from the VDR or S-VDR to a laptop computer. Manufacturers are required to provide software for extracting data, instructions for extracting data, and cables for connecting between a recording device and computer.
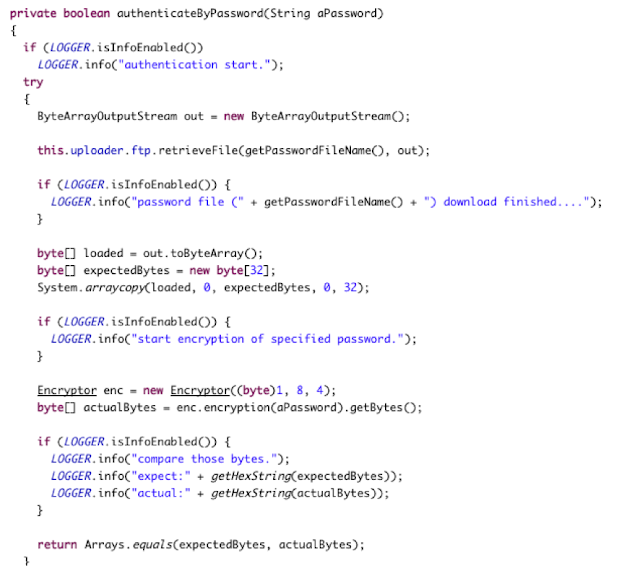
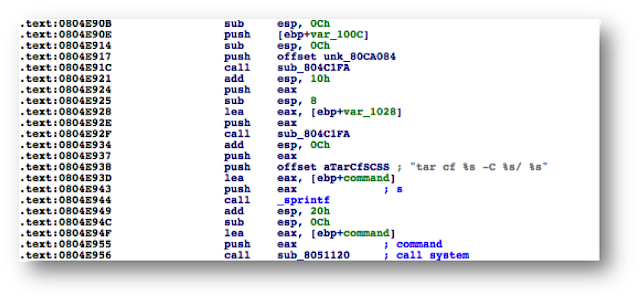
Take this function, extracted from from the Playback software, as an example of how not to perform authentication. For those who are wondering what ‘Encryptor’ is, just a word: Scytale.
VR-3000’s firmware can be updated with the help of Windows software known as ‘VDR Maintenance Viewer’ (client-side), which is proprietary Furuno software.
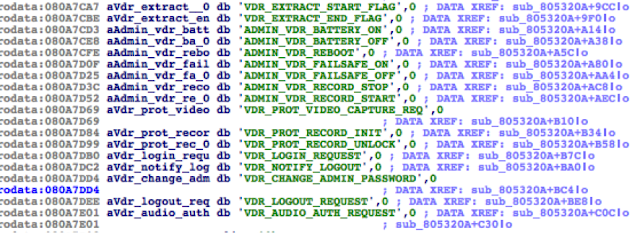
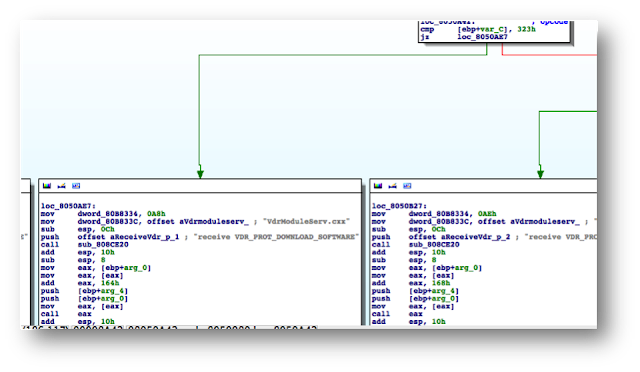
The VR-3000 firmware (server-side) contains a binary that implements part of the firmware update logic: ‘moduleserv’
This service listens on 10110/TCP.
Internally, both server (DCU) and client-side (VDR Maintenance Viewer, LivePlayer, etc.) use a proprietary session-oriented, binary protocol. Basically, each packet may contain a chain of ‘data units’, which, according to their type, will contain different kinds of data.
At this point, attackers could modify arbitrary data stored on the DCU in order to, for example, delete certain conversations from the bridge, delete radar images, or alter speed or position readings. Malicious actors could also use the VDR to spy on a vessel’s crew as VDRs are directly connected to microphones located, at a minimum, in the bridge.
Before IMO’s resolution MSC.233(90) [3], VDRs did not have to comply with security standards to prevent data tampering. Taking into account that we have demonstrated these devices can be successfully attacked, any data collected from them should be carefully evaluated and verified to detect signs of potential tampering.
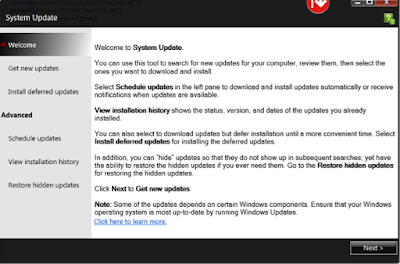
Privilege Escalation Vulnerabilities Found in Lenovo System Update
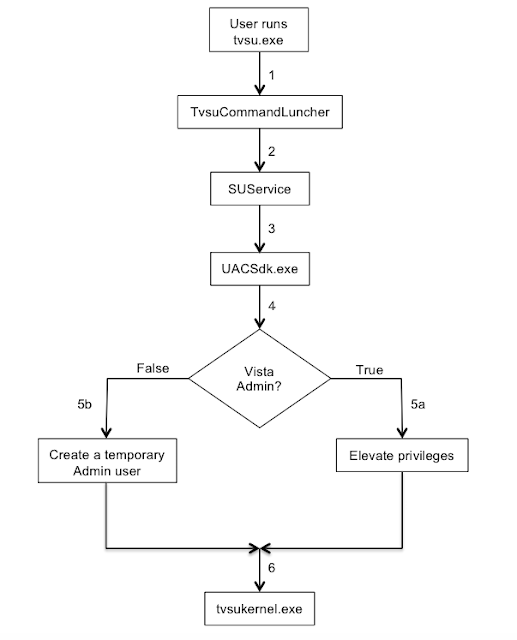
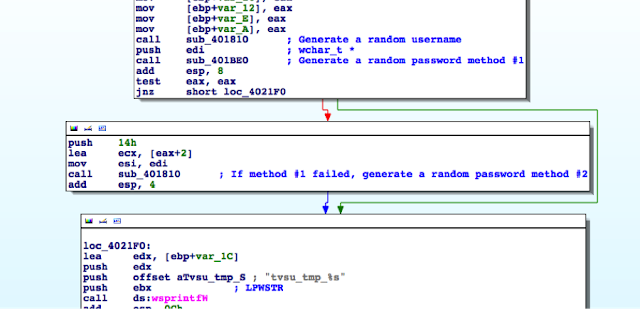
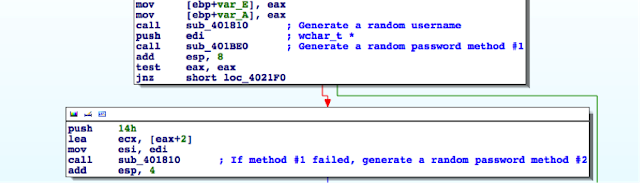
1 – The user starts System Update by running the tvsu.exe binary which runs the TvsuCommandLauncher.exe with a specific argument. Previously, Lenovo fixed vulnerabilities that IOActive discovered where an attacker could impersonate a legitimate caller and pass the command to be executed to the SUService service through named pipes to gain a privilege escalation. In the newer version, the argument is a number within the range 1-6 that defines a set of tasks within the dll TvsuServiceCommon.dll
2 – TvsuCommandLauncher.exe then, as usual, contacts the SUService service that is running with System privileges, to process the required query with higher privileges.
3 – The SUService service then launches the UACSdk.exe binary with System privileges to prepare to execute the binary and run the GUI interface with Administrator privileges.
4 – UACSdk.exe checks if the user is a normal unprivileged user or a Vista Administrator with the ability to elevate privileges.
5 – Depending on user privileges:
-
- For a Vista Admin user, the user’s privileges are elevated.
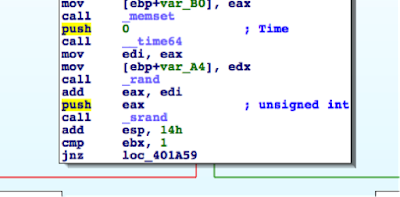
- For an unprivileged user, UACSdk.exe creates a temporary Administrator account with a random password which is deleted it once the application is closed.
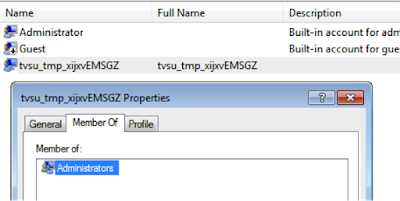
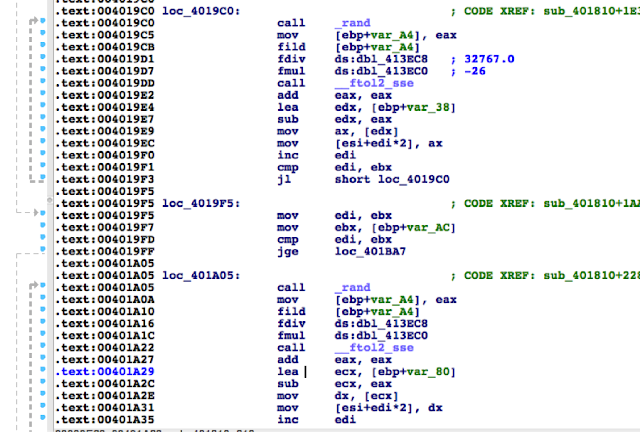
The username for the temporary Administrator account follows the pattern tvsu_tmp_xxxxxXXXXX, where each lowercase x is a randomly generated lower case letter and each uppercase X is a randomly generated uppercase letter. A 19-byte, random password is generated.
Here is a sample of a randomly created user:
6 – Through tvsukernel.exe binary, the main Lenovo System Update GUI application is then run with Administrator privileges.
1 – The link in the main application interface
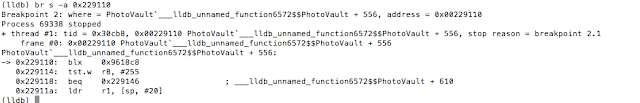
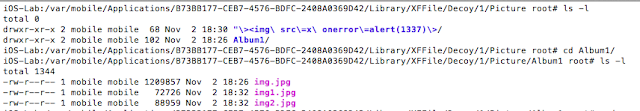
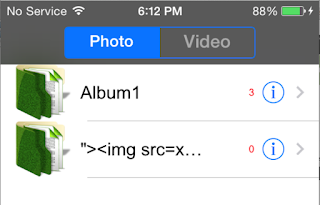
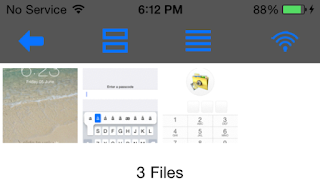
Breaking into and Reverse Engineering iOS Photo Vaults
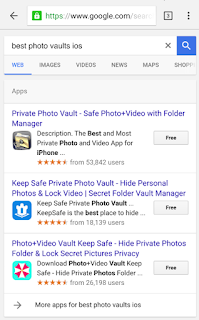
Every so often we hear stories of people losing their mobile phones, often with sensitive photos on them. Additionally, people may lend their phones to friends only to have those friends start going through their photos. For whatever reason, a lot of people store risqué pictures on their devices. Why they feel the need to do that is left for another discussion. This behavior has fueled a desire to protect photos on mobile devices.
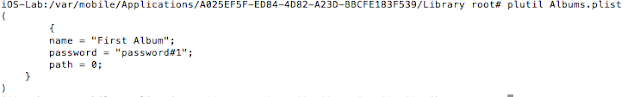
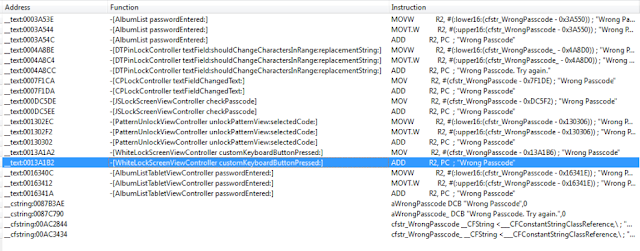
One popular option are photo vault applications. These applications claim to protect your photos, videos, etc. In general, they create albums within their application containers and limit access with a passcode, pattern, or, in the case of newer devices, TouchID.
- Jailbroken iPhone 4S (7.1.2)
- BurpSuite Pro
- Hex editor of choice
- Cycript
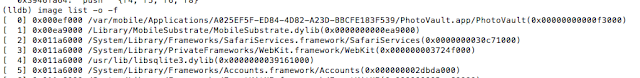
- Private Photo Vault
- Photo+Video Vault Keep Safe(My Media)
- KeepSafe
- IDA Pro/Hopper
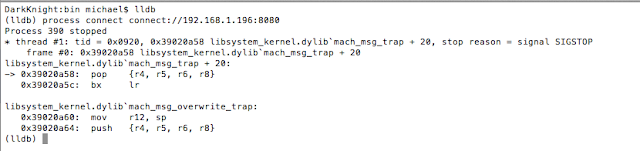
- LLDB
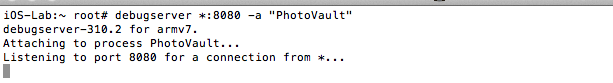
- Usbmuxd
- Debugserver
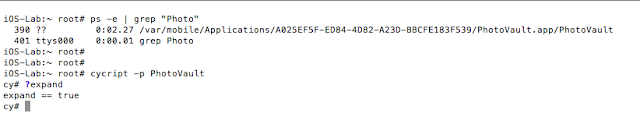
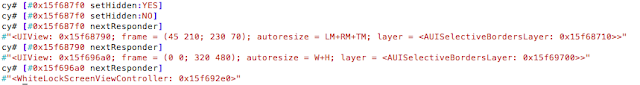
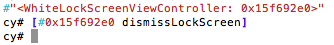
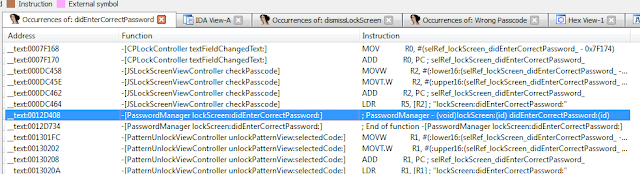
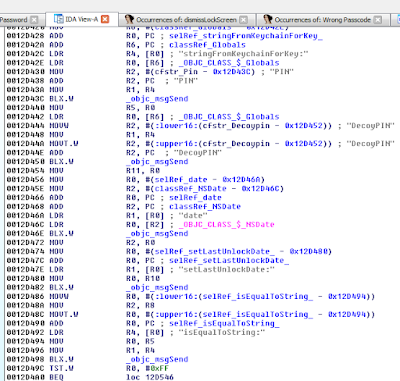
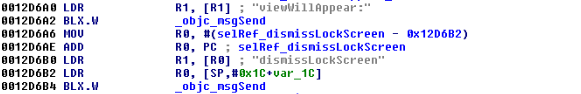
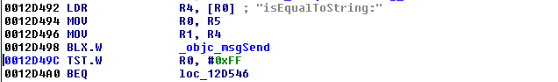
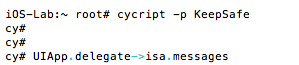
- cycript to bypass the lock screens
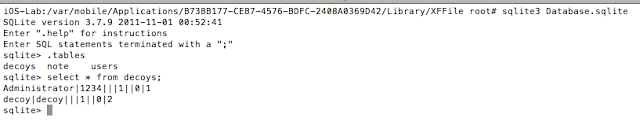
- sqlite to extract sensitive information from the application databases
- plutil to read plist files and access sensitive information
- BurpSuite Pro to intercept traffic from the application
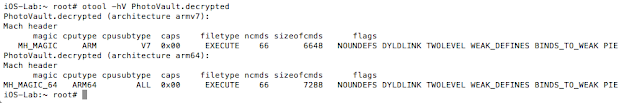
- IDA Pro to reverse the binary and achieve results similar to cycript
- No jailbreak detection routines
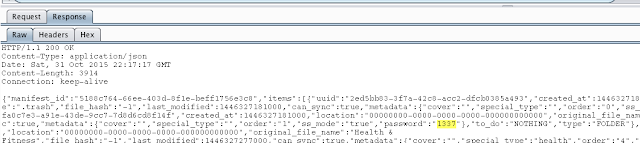
- Insecure storage of credentials
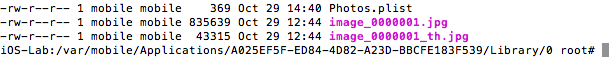
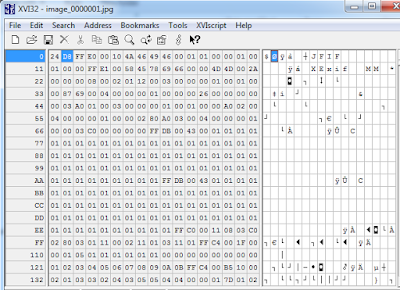
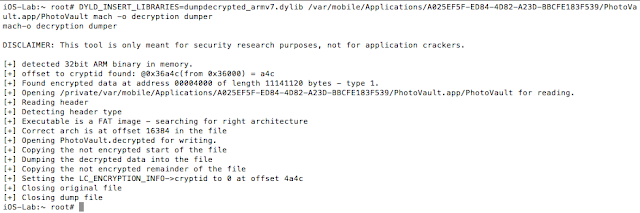
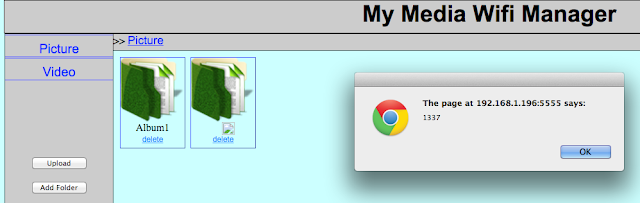
- Photos stored unencrypted
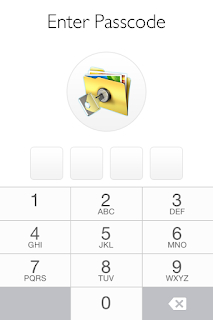
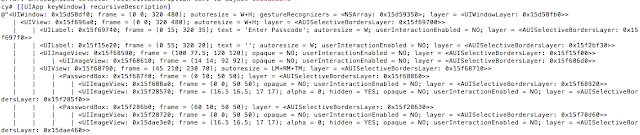
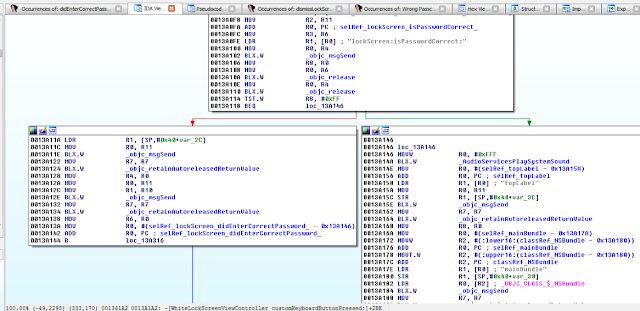
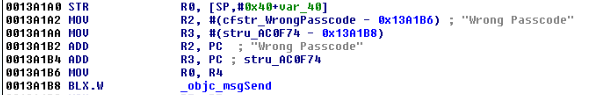
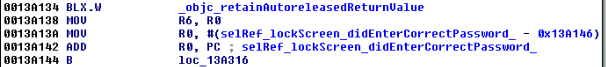
- Lock screens are easy to bypass
- Common web application vulnerabilities
- http://www.zdziarski.com/blog/?p=3951
- Hacking and Securing iOS Applications: Stealing Data, Hijacking Software, and How to Prevent It
- http://www.cycript.org/
- http://cgit.sukimashita.com/usbmuxd.git/snapshot/usbmuxd-1.0.8.tar.gz
- http://resources.infosecinstitute.com/ios-application-security-part-42-lldb-usage-continued/
- https://github.com/stefanesser/dumpdecrypted
- https://developer.apple.com/library/ios/technotes/tn2239/_index.html#//apple_ref/doc/uid/DTS40010638-CH1-SUBSECTION34
- https://developer.apple.com/library/ios/documentation/UIKit/Reference/UIResponder_Class/#//apple_ref/occ/instm/UIResponder/nextResponder
Lenovo TVSUkernel Escalation of Privileges
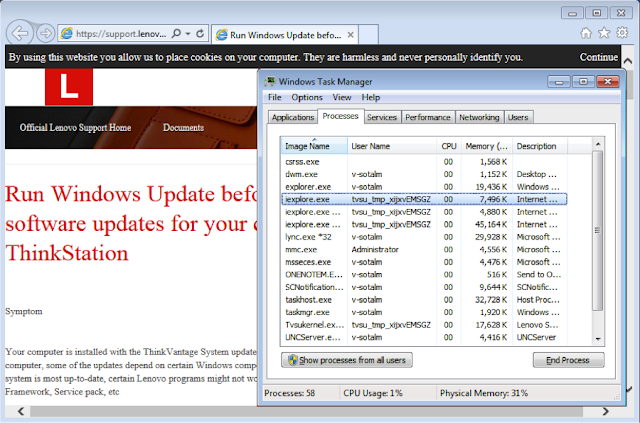
The Lenovo System Update allows least-privileged users to perform system updates. To do this, System Update includes the System Update service (SUService.exe). This service runs as the privileged SYSTEM user, creates a temporary user account with Administrator privileges, and starts a GUI application (Tvsukernel.exe) with the new Administrator account. Once the application is closed, the temporary Administrator account is appropriately deleted. However the GUI application contains links to online support and privacy help topics, which, when clicked, start a web browser instance under the temporary Administrator account to display the online topic.
As a result, an attacker who is unprivileged can exploit the web browser instance that is running as Administrator to elevate his or her own privileges to Administrator or SYSTEM. (more…)
Lenovo System Update Created an Insecure Random Administrator Password
This vulnerability allows a local unprivileged user to elevate privileges to Administrator or SYSTEM. Since the user is running the System Update is an unprivileged user, the SUService that is running as System will run the UACsdk.exe binary to create a temporary Administrator account to run the GUI application (Tvsukernel.exe). (more…)
Five Reasons Why You Should Go To BruCON
BruCON is one of the most important security conferences in Europe. Held each October, the ‘Bru’ in ‘BruCON’ refers to Brussels, the capital of Belgium, where it all started. Nowadays, it’s held in the beautiful city of Ghent, just 55 mins from its origin. I had the chance to attend this year, and here are the five things that make it a great conference, in my opinion.
(Shyama Rose talking about BASE jumping and risk)
While paid trainings take place two or three days before the conference, free workshops are available to the public during the two-day conference.
«Escalating Privileges Through Better Communication»)
Harman-Kardon UConnect Vulnerability
UConnect 8.4AN/RA3/RA4 are vehicle-based infotainment systems. UConnect systems are integrated in certain makes of Chrysler, Dodge, Jeep, and Ram vehicles.
The UConnect infotainment system allowed an unauthenticated connection from other access points on the Sprint Network. An attacker could issue commands to other components within the vehicle through the infotainment system. (more…)
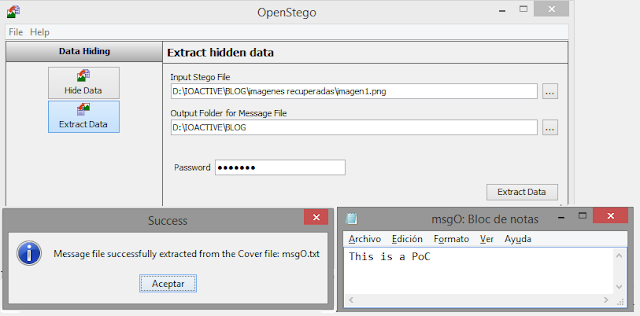
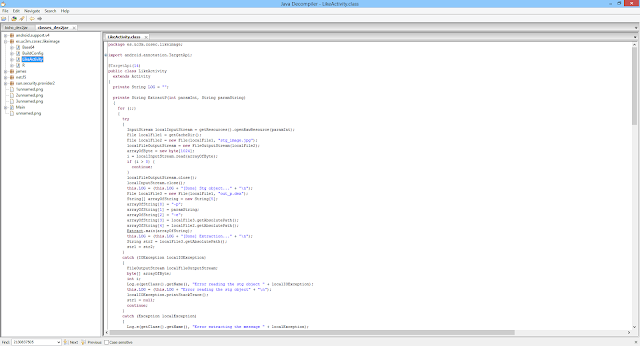
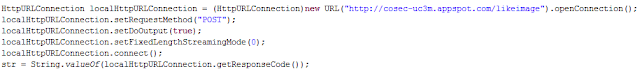
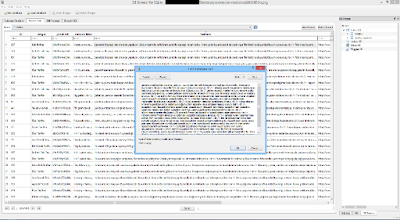
Is Stegomalware in Google Play a Real Threat?
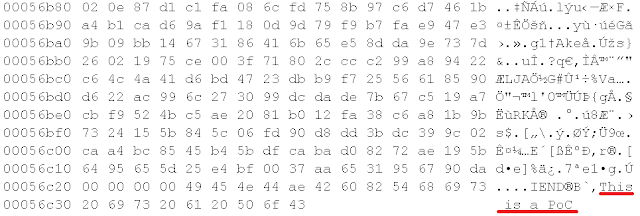
Step 2. Analyzing the current and previous version of this app, I discover connections to specific URLs (images files). Are these truly images? Not all.
Step 4. If we analyze these databases, it is possible to find curious messages. For example, recipes with drugs.
Disclaimer: part of this research is based on a previous research by the author at ElevenPaths
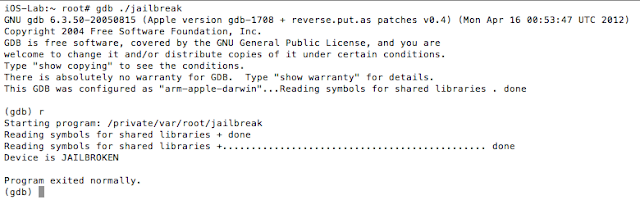
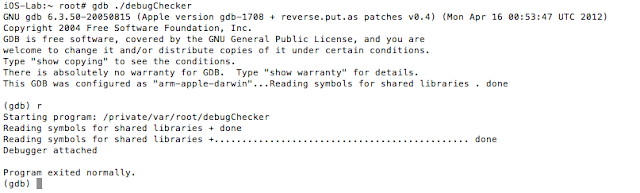
The iOS Get out of Jail Free Card
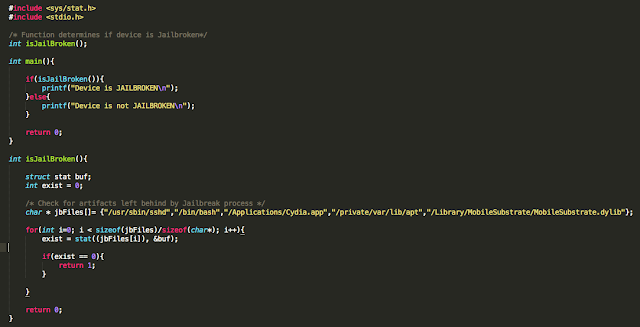
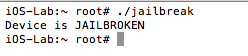
Well, iOS mobile application assessments usually occur on jailbroken devices, and application developers often implement measures that seek to thwart this activity. The tester often has to come up with clever ways of bypassing detection and breaking free from this restriction, a.k.a. “getting out of jail”. This blog post will walk you through the steps required to identify and bypass frequently recommended detection routines. It is intended for persons who are just getting started in reverse engineering mobile platforms. This is not for the advanced user.
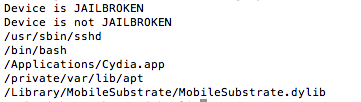
- Known file paths
- Use of non-default ports such as port 22(OpenSSH), which is often used to connect to and administer the device
- Symbolic links to various directories (e.g. /Applications, etc.)
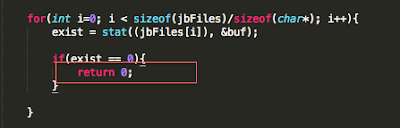
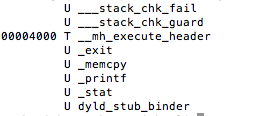
- Integrity of the sandbox (i.e. a call to fork() should return a negative value in a properly functioning sandbox)
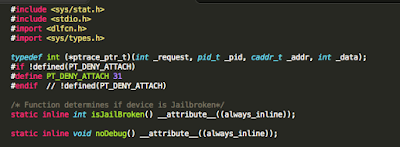
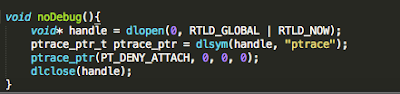
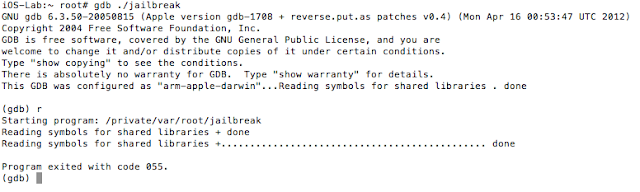
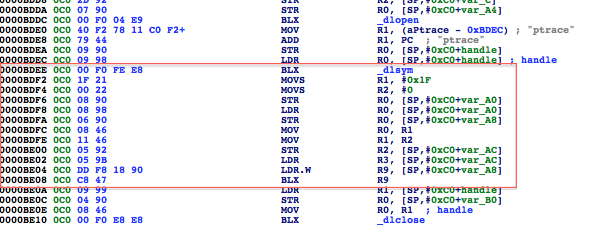
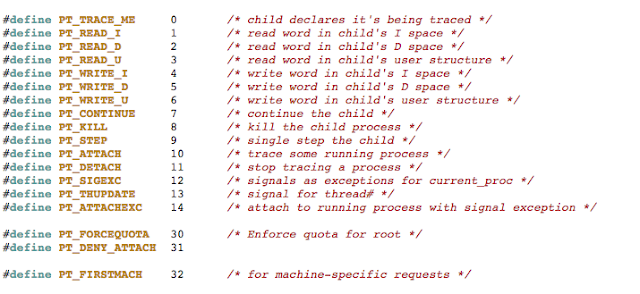
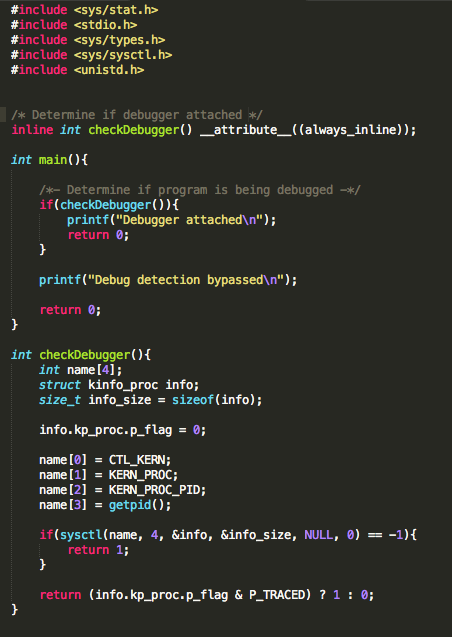
In addition to the above, developers will often seek to prevent us from debugging the process with the use of PT_ATTACH_DENY, which prevents the use of the ptrace() system call (a call used in the debugging of iOS applications). The point is, there are a multitude of ways developers try to thwart our efforts as pen testers. That discussion, however, is beyond the scope of this post. You are encouraged to check out the resources included in the references section. Of the resources listed, The Mobile Application Hackers Handbook does a great job covering the topic.
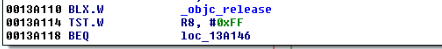
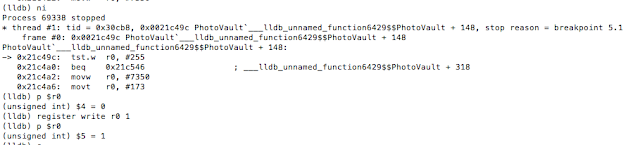
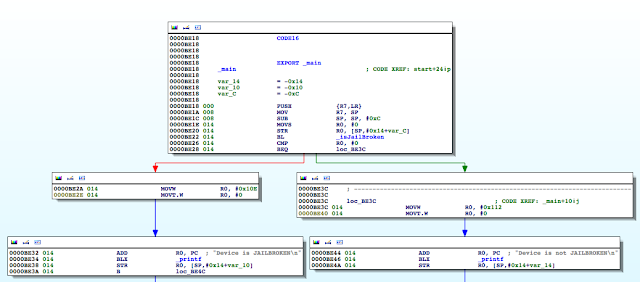
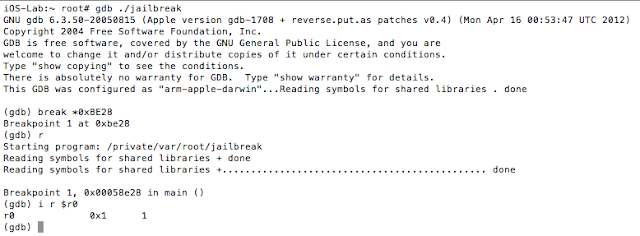
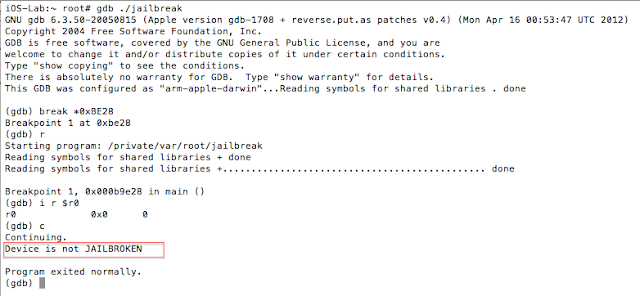
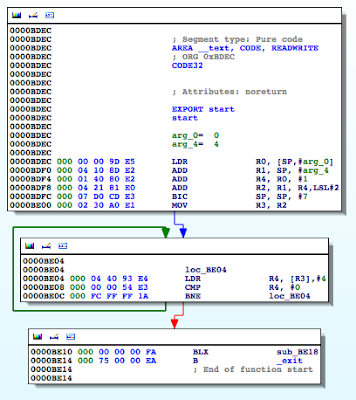
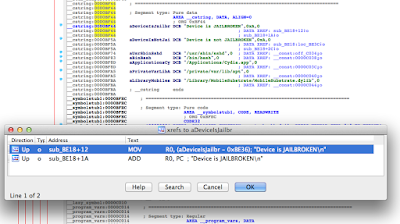
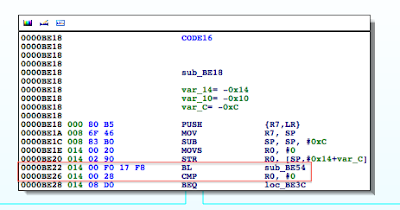
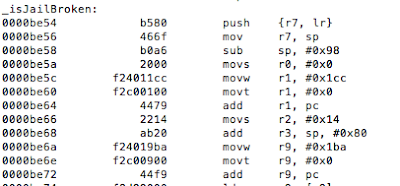
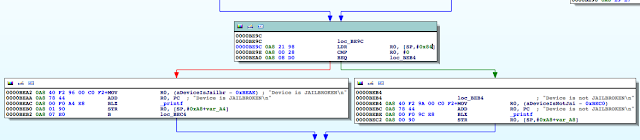
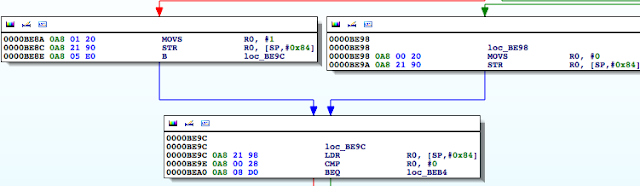
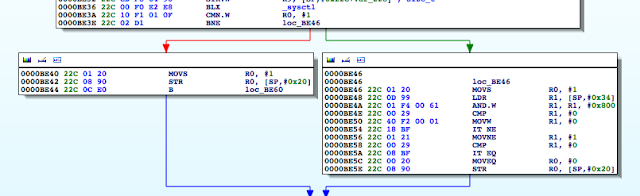
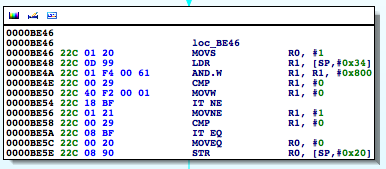
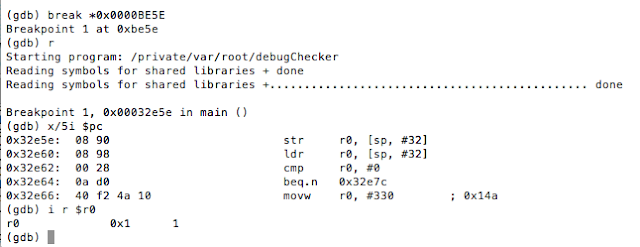
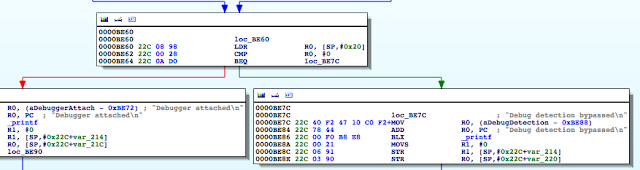
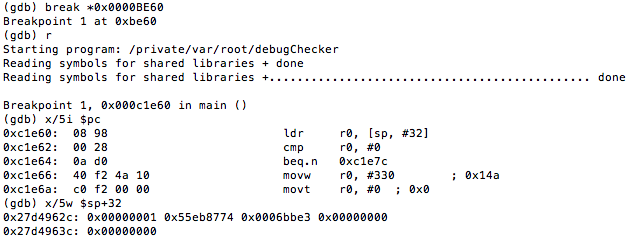
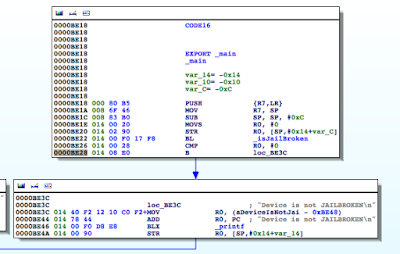
Figure 5: Examining the contents of the R0 register
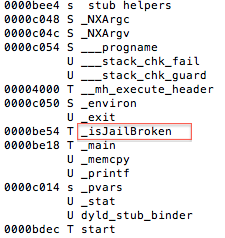
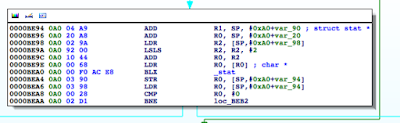
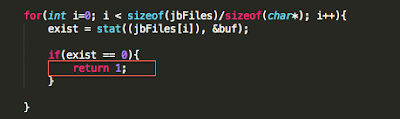
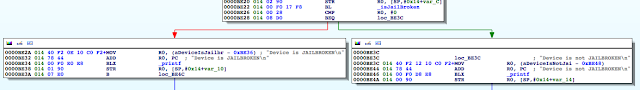
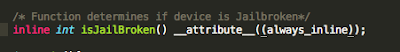
Figure 6: isJailBroken function analysis
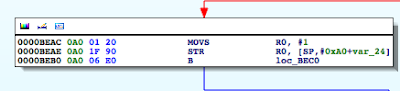
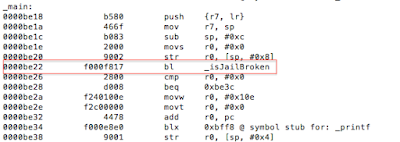
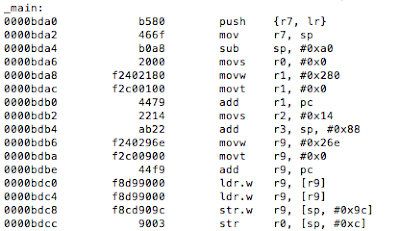
Figure 7: Determining where R0 register is set
- http://www.amazon.com/The-Mobile-Application-Hackers-Handbook/dp/1118958500
- http://www.amazon.com/Practical-Reverse-Engineering-Reversing-Obfuscation/dp/1118787315
- http://www.amazon.com/Hacking-Securing-iOS-Applications-Hijacking/dp/1449318746
- https://www.owasp.org/index.php/IOS_Application_Security_Testing_Cheat_Sheet
- https://www.theiphonewiki.com/wiki/Bugging_Debuggers
- http://www.opensource.apple.com/source/xnu/xnu-792.13.8/bsd/sys/ptrace.h