Year: 2014
Upcoming Blackhat & DEF CON talk: A Survey of Remote Automotive Attack Surfaces
Hi Internet,
Chris Valasek here; you may remember me from such movies as ‘They Came to Burgle Carnegie Hall’. In case you haven’t heard, Dr. Charlie Miller and I will be giving a presentation at Black Hat and DEF CON titled ‘A Survey of Remote Automotive Attack Surfaces’. You may have seen some press coverage on Wired, CNN, and Dark Reading several days ago. I really think they all did a fantastic job covering what we’ll be talking about.
We are going to look at a bunch of cars’ network topology, cyber physical features, and remote attack surfaces. We are also going to show a video of our automotive intrusion prevention/detection system.
While I’m sure many of you want find out which car we think is most hackable (and you will), we don’t want that to be the focus of our research. The biggest problem we faced while researching the Toyota Prius and Ford Escape was the small sample set. We were able to dive deeply into two vehicles, but the biggest downfall was only learning about two specific vehicles.
Our research and presentation focus on understanding the technology and implementations, at a high level, for several major automotive manufacturers. We feel that by examining how different manufacturers design their automotive networks, we’ll be able to make more general comments about vehicle security, instead of only referencing the two aforementioned automobiles.
I hope to see everyone in Vegas and would love it if you show up for our talk. It’s at 11:45 AM in Lagoon K on Wednesday August 6.
— CV
P.S. Come to the talk for some semi-related, never-before-seen hacks.
Hacking Washington DC traffic control systems
This is a short blog post, because I’ve talked about this topic in the past. I want to let people know that I have the honor of presenting at DEF CON on Friday, August 8, 2014, at 1:00 PM. My presentation is entitled “Hacking US (and UK, Australia, France, Etc.) Traffic Control Systems”. I hope to see you all there. I’m sure you will like the presentation.
I am frustrated with Sensys Networks (vulnerable devices vendor) lack of cooperation, but I realize that I should be thankful. This has prompted me to further my research and try different things, like performing passive onsite tests on real deployments in cities like Seattle, New York, and Washington DC. I’m not so sure these cities are equally as thankful, since they have to deal with thousands of installed vulnerable devices, which are currently being used for critical traffic control.
The latest Sensys Networks numbers indicate that approximately 200,000 sensor devices are deployed worldwide. See http://www.trafficsystemsinc.com/newsletter/spring2014.html. Based on a unit cost of approximately $500, approximately $100,000,000 of vulnerable equipment is buried in roads around the world that anyone can hack. I’m also concerned about how much it will cost tax payers to fix and replace the equipment.
One way I confirmed that Sensys Networks devices were vulnerable was by traveling to Washington DC to observe a large deployment that I got to know.
When I exited the train station, the fun began.
DC22 Talk: Killing the Rootkit
By Shane Macaulay
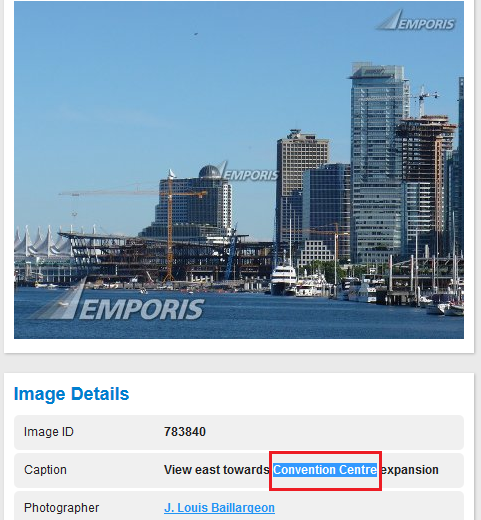
A Survey of Remote Automotive Attack Surfaces
By looking at each car’s remote attack surface, internal network architecture, and computer controlled features, we are able to draw some conclusions about the suitability of the vehicle to remote attack. This doesn’t mean that the most susceptible looking isn’t in fact quite secure (i.e. coded very securely) or that the most secure looking isn’t in fact trivially exploitable, but it does provide some objective measure of the security of a large number of vehicles that wouldn’t be possible to examine in detail without a massive effort. It also provides an outline on how to design and construct secure vehicles, namely in making each of these three stages of exploitation as difficult as possible.
The authors also discuss different strategies to securing vehicles from remote attack in a layered, attack resilient fashion. In particular, it introduces a device that acts like a network intrusion detection and prevention device as well as discusses some early testing results.
Lastly, to the authors’ knowledge, this is the first publicly available resource for automotive network architecture review. While network architecture review is commonplace in modern network/computer security, much of automobile topology has been shrouded in secrecy.
Belkin WeMo Home Automation Vulnerabilities
The WeMo devices connect to the Internet using the STUN/TURN protocol. This gives users remote control of the devices and allows them to perform firmware updates from anywhere in the world. A generated GUID is the primary source of access control.
WeMo also uses a GPG-based, encrypted firmware distribution scheme to maintain device integrity during updates. Unfortunately, attackers can easily bypass most of these features due to the way they are currently implemented in the WeMo product line. The command for performing firmware updates is initiated over the Internet from a paired device. Also, firmware update notices are delivered through an RSS-like mechanism to the paired device, rather than the WeMo device itself, which is distributed over a non-encrypted channel. As a result, attackers can easily push firmware updates to WeMo users by spoofing the RSS feed with a correctly signed firmware. (more…)
Steam Client Creates World-writable Shell Script
While performing a routine world-writable file scan, one of IOActive’s consultants discovered that the Steam Client for Mac OS X creates world-writable shell scripts when installing games. (more…)
OleumTech Wireless Sensor Network Vulnerabilites
OleumTech has manufactured industrial wireless solutions for almost 15 years, providing visibility to disparate assets for major Oil & Gas producers for near real-time optimization decisions, resource deployment, and regulatory compliance. OleumTech also manufacturers industrial automation systems that represents the new paradigm of remote monitoring and control for industries, such as Oil & Gas, Refining, Petro-chemical, Utilities, and Water/Wastewater.
In June 2013, IOActive Labs reported four critical vulnerabilities in OleumTech’s wireless sensor network to ICS-CERT. To date, IOActive Labs is not aware of any fixes released by OleumTech. (more…)
Video: Building Custom Android Malware for Penetration Testing
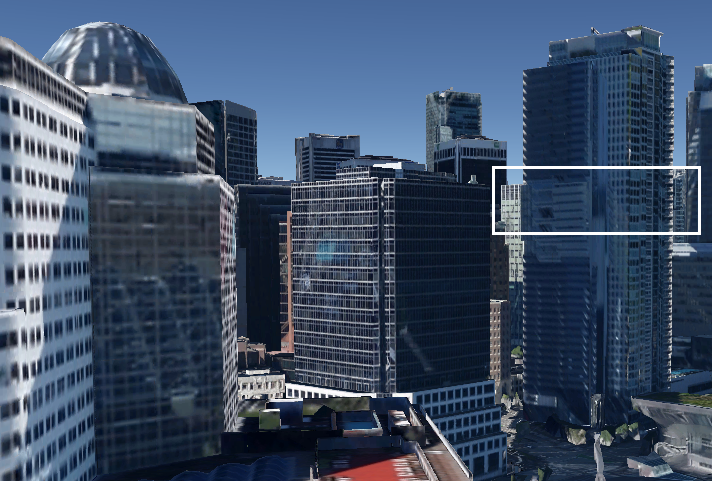
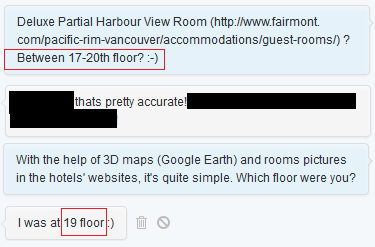
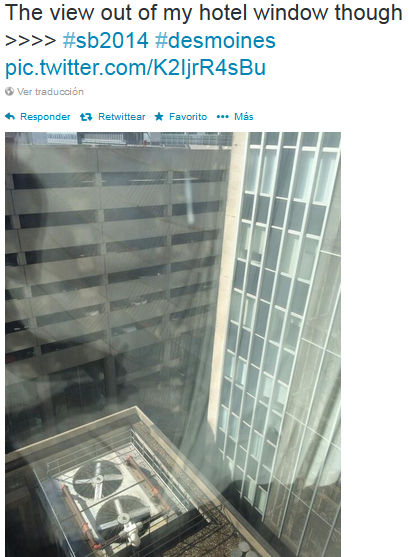
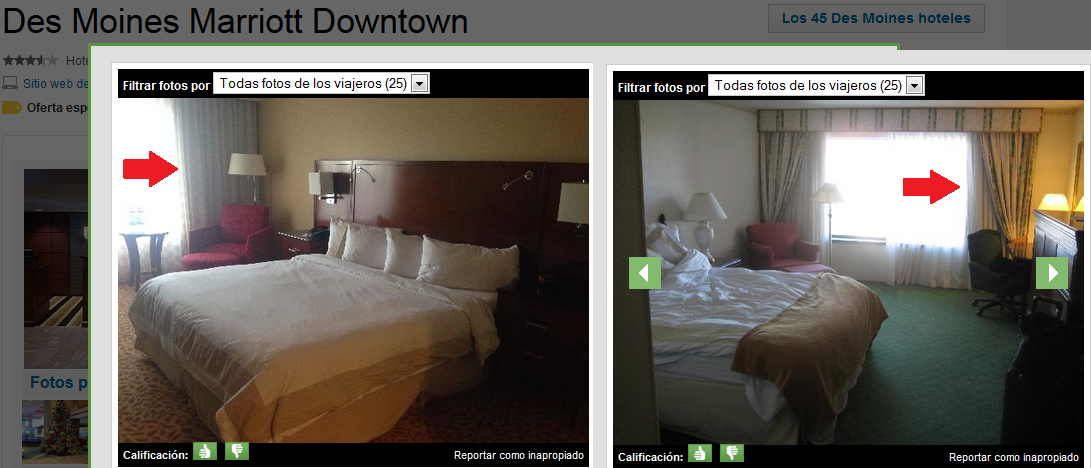
Glass Reflections in Pictures + OSINT = More Accurate Location
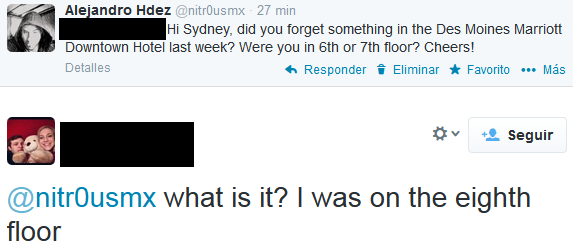
By Alejandro Hernández – @nitr0usmx
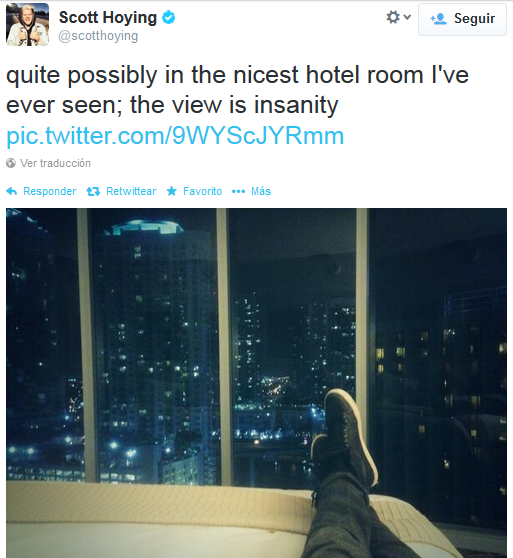
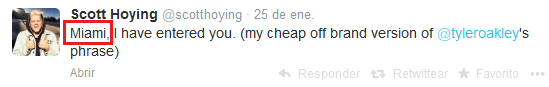
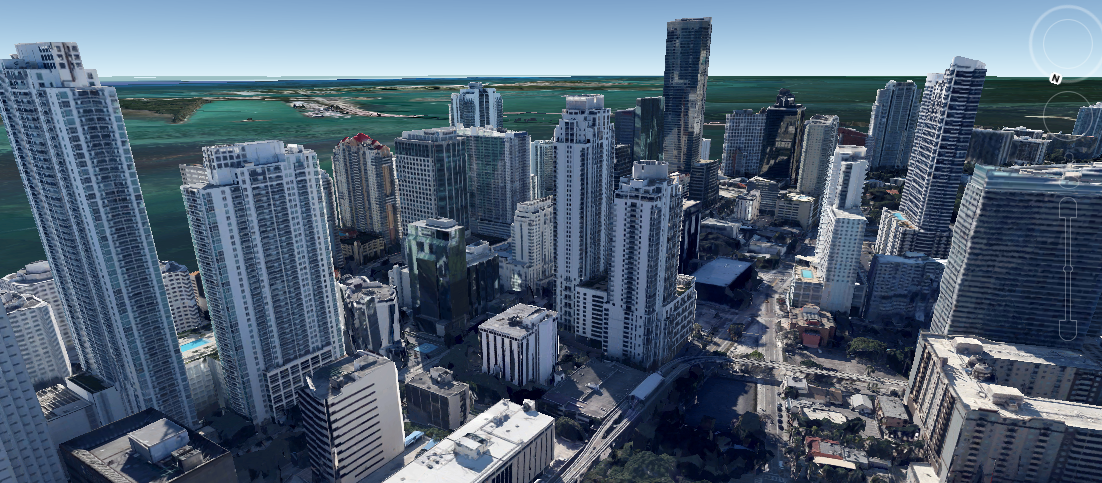
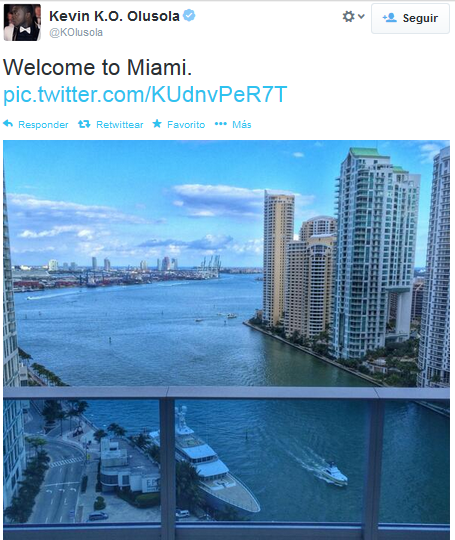
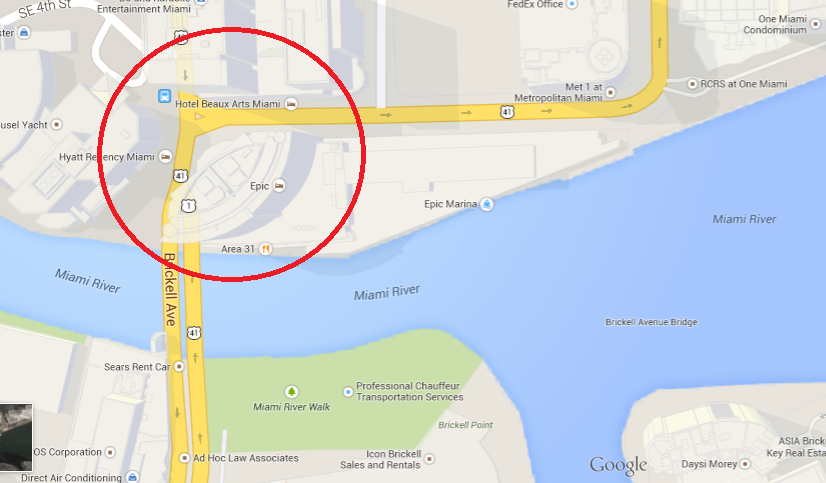
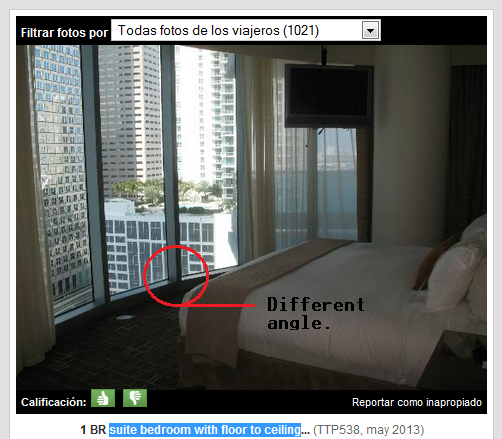
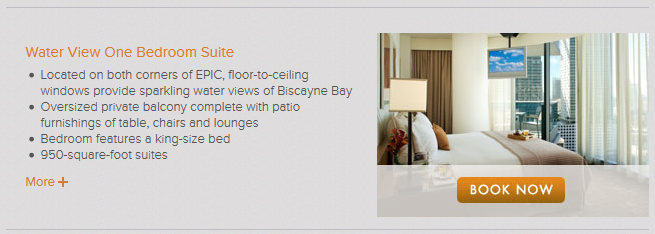
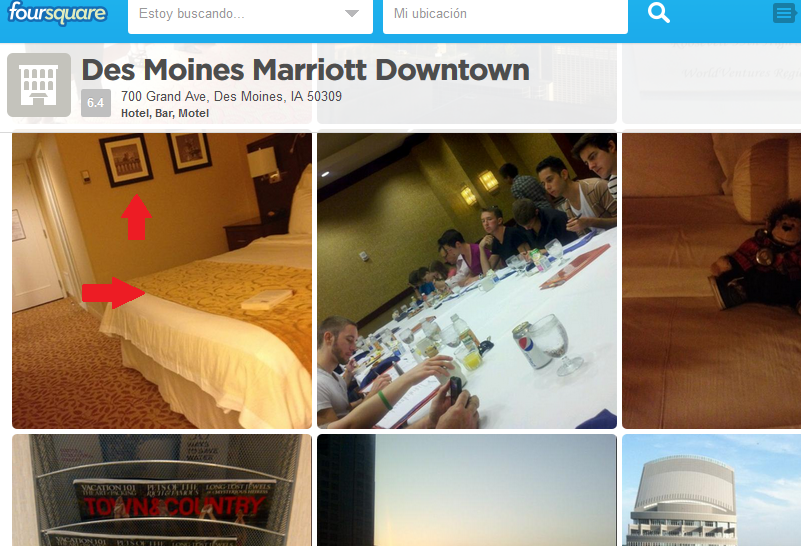
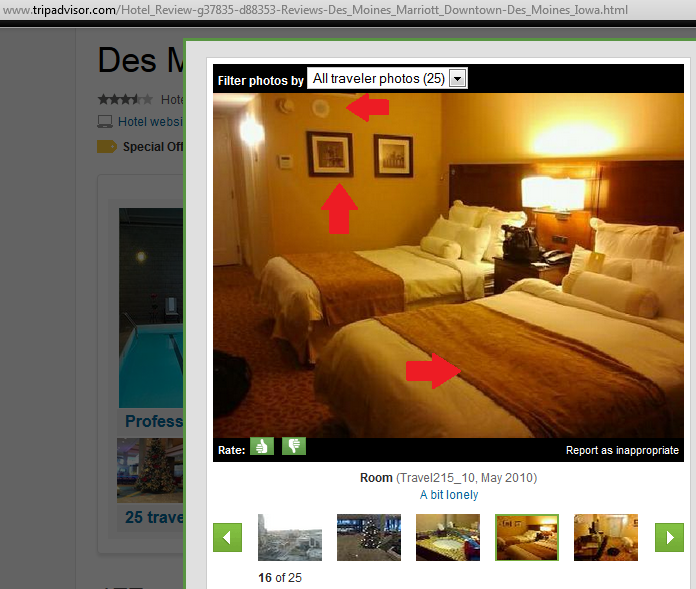
Disclaimer: The aim of this article is to help people to be more careful when taking pictures through windows because they might reveal their location inadvertently. The technique presented here might be used for many different purposes, such as to track down the location of the bad guys, to simply know in which hotel is that nice room or by some people, to follow the tracks of their favorite artist.
All of the pictures presented here were posted by the owners on Twitter. The tools and information used to determine the locations where the pictures were taken are all publically available on the Internet. No illegal actions were performed in the work presented here.