Independent researchers Carlos Hollmand and Dillon Beresford identified multiple vulnerabilities in WellinTech’s KingView and a single vulnerability in WellinTech’s KingHistorian applications. These vulnerabilities can be exploited remotely. WellinTech has created a patch, and the researchers have validated that the patch resolves these vulnerabilities in the KingView and KingHistorian applications. (more…)
Year: 2012
Reversal and Analysis of the Zeus and SpyEye Banking Trojans
Although the core functionality of SpyEye is similar to its main rival Zeus, SpyEye incorporates many advanced tricks to hide its presence on the local system. This document includes a deep technical analysis of the bot’s advanced hooking and injection mechanisms, as well as its core functionality used to hijack and steal user information.
Zeus is an advanced piece of malware, so getting it to a reversible state was not a trivial exercise since it incorporates multiple layers of custom, portable, executable encryption. IOActive reverse engineers stripped each encryption layer and rebuilt the executable to allow for proper disassembly. Once Zeus was in an unpacked state, consultants identified additional roadblocks including non-existent import address tables, obfuscated string tables, and relocated code. Zeus included many methods to hinder reverse engineering. (more…)
Wonderware Archestra ConfigurationAccessComponent ActiveX stack overflow
The Wonderware Archestra ConfigurationAccessComponent ActiveX control that is marked “safe for scripting” is suffering from a stack-overflow vulnerability. The UnsubscribeData method of the IConfigurationAccess interface is using wcscpy() to copy its first parameter into a static-sized local buffer. Attackers can exploit this vulnerability to overwrite arbitrary stack data and gain code execution. (more…)
XBMC File Traversal Vulnerability
XBMC is an award-winning, free, and open source (GPL) software media player and entertainment hub for digital media. XBMC is available for Linux, OSX, and Windows. Created in 2003 by a group of like-minded programmers, XBMC is a nonprofit project run and was developed by volunteers located around the world. More than 50 software developers have contributed to XBMC, and 100-plus translators have worked to expand its reach, making it available in more than 30 languages. (more…)
Multiple Vulnerabilities in Fwknop
Fwknop stands for the “FireWall KNock OPerator” and implements an authorization scheme called Single Packet Authorization (SPA). This method of authorization is based on a default-drop packet filter and libpcap. A server might appear to have no open ports available, but it could still grant access to certain services if authorized fwknop packets are received. Companies commonly use this service on exposed systems and need to diminish the attack surface of this service.
wknop contains several vulnerabilities. The most critical of these might allow remote, authenticated attackers to leverage flaws to execute code and produce denial-of-service conditions. (more…)
IBM Informix XML functions overflows
Informix is one of the world’s most widely used database servers, with users ranging from the world’s largest corporations to startups. Informix incorporates design concepts that are significantly different from traditional relational platforms. This results in extremely high levels of performance and availability, distinctive capabilities in data replication and scalability, and minimal administrative overhead.
Informix contains two vulnerabilities affecting several versions. Attackers can exploit these vulnerabilities to execute arbitrary code or cause denial-of-service conditions. (more…)
Windows Kernel Library Filename Parsing Vulnerability
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Windows. User interaction is required to exploit this vulnerability in that the target must open or browse to a file or subfolder with a specially crafted name on a network SMB share, UNC share, or WebDAV web folder. (more…)
Inside Flame: You Say Shell32, I Say MSSECMGR
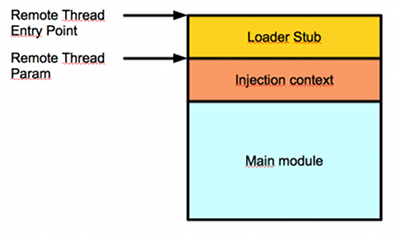
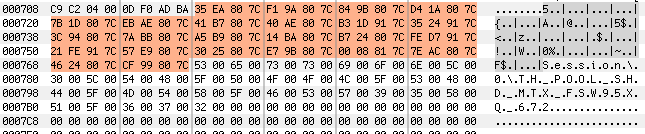
explorer.exe than winlogon.Shell32.dll in this case.LoadLibrary, to avoid being detected as an active module.DDEnumCallback is called, Flame injects a blob and creates a remote thread in Services.exe. The blob has the following structure:dllloader.cpp[2] with some additional tricks.The injection context is a defined structure that contains all the information the loader stub may need including API addresses or names, DLL names, and files—in fact, the overall idea reminded me of Didier Stevens’ approach to generating shellcodes directly from a C compiler[3]
Injection Context: Blob + 0x710
API Addresses:
|
esi OpenMutexW
esi+4 VirtualAlloc
esi+8 VirtualFree
esi+0Ch VirtualProtect
esi+10h LoadLibraryA
esi+14h LoadLibraryW
esi+18h GetModuleHandleA
esi+1Ch GetProcAddress
esi+20h memcpy
esi+24h memset
esi+28h CreateFileMappingW
esi+2Ch OpenFileMappingW
|
esi+30h MapViewOfFile
esi+34h UnmapViewOfFile
esi+38h ReleaseMutex
esi+3Ch NtQueryInformationProcess
esi+40h GetLastError
esi+44h CreateMutexW
esi+48h WaitForSingleObject
esi+4Ch CloseHandle
esi+50h CreateFileW
esi+54h FreeLibrary
esi+58h Sleep
esi+5Ch LocalFree
|
Shell32.dll: A matter of VAD
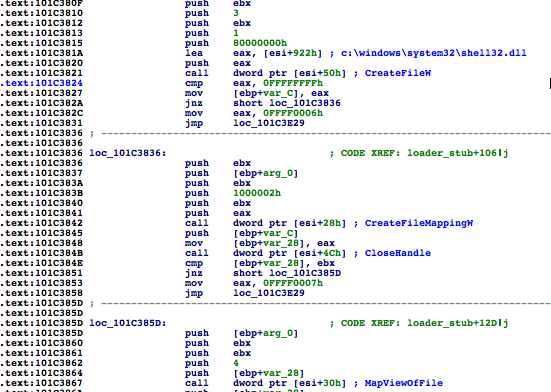
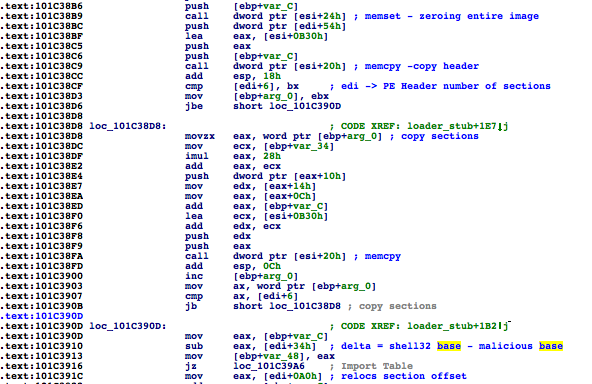
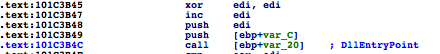
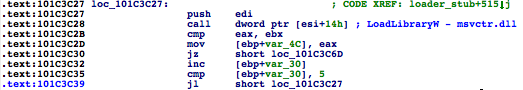
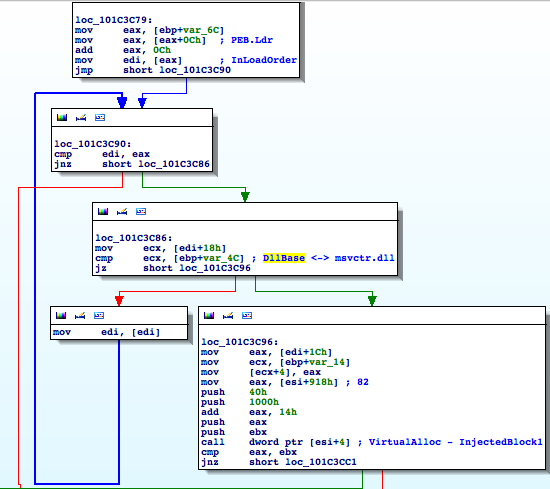
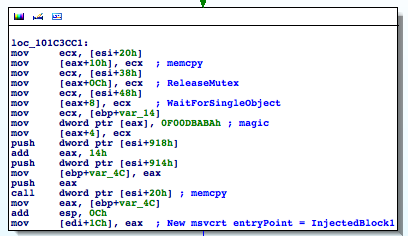
Shell32.dll, which is one of the largest DLLs you can find on any Windows system, meaning it’s large enough to hold Flame across different versions.shell32.dll has been mapped, a VAD node is created that contains a reference to the FILE_OBJECT, which points to Shell32.dll. Flame then zeroes that memory and loads its malicious module through the custom PE loader, copying sections, adjusting permissions, and fixing relocations.Shell32.dll, a trusted module, when it’s actually mssecmgr.ocx.DllEntryPoint, passing in DLL_PROCESS_ATTACH to initialize the DLL.DLL_THREAD_ATTACH, DLL_THREAD_DETACH, and DLL_PROCESS_DETACH.msvcrt.dll is loaded up to five times, which is a little bit weird, no?InLoadOrder structure is traversed to find the entry that corresponds to msvcrt.dll by comparing the DLL base addresses:InjectedBlock1 (0x101C36A1) is a small piece of code that basically dispatches the events received to both the malicious DLL and the original module. msvcrt.dll several times to increase its reference count to prevent msvcrt.dll from being unloaded, since this hook would then become useless.Thoughts on FIRST Conference 2012
I recently had the opportunity to attend the FIRST Conference in Malta and meet Computer Emergency Response Teams from around the world. Some of these teams and I have been working together to reduce the internet exposure of Industrial Control Systems, and I met new teams who are interested in the data I share. For those of you who do not work with CERTs, FIRST is the glue that holds together the international collaborative efforts of these teams—they serve as both an organization that makes trusted introductions, and vets new teams or researchers (such as myself).
Old Tricks, New Targets
Just a few days ago, Digitalbond announced that they had been victims of a spear phishing attack. An employee received an email linking to a malicious zip file, posing as a legitimate .pdf paper related to industrial control systems security. Therefore, the bait used by the attackers was supposedly attracting targets somehow involved with the ICS community. (more…)