
TL; DR: Modern mobile OSes encrypt data by default, nevertheless, the defense-in-depth paradigm dictates that developers must encrypt sensitive data regardless of the protections offered by the underlying OS. This is yet another case study of data stored unencrypted, and most importantly, a reminder to developers not to leave their apps’ data unencrypted. In this case study, physical access to an unlocked phone, trusted computer or unencrypted backups of an iPhone is required to exfiltrate the data, which in turn does not include authentication data and cannot be used to control or track the vehicle in any way.
Introduction
“While modern mobile operating systems allow encrypting mobile devices, which users can use to protect themselves, it is ultimately the developer’s responsibility to make sure that their software is thoroughly safeguarded. To this end, developers should provide reliable mobile app data encryption that leaves no user data without protection.” — Dmitriy Smetana.
Physical theft is not the only attack vector that threatens the data stored on a mobile phone. Imagine, for instance, a shared computer at home or in the office where a phone has been authenticated and trusted. When the phone is connected and authenticated, a malicious actor with access to this computer would be able to extract its apps’ data. The likelihood is low in the real world, though.
One day during the pandemic I was wondering if my car’s mobile app was encrypting the data or not. So, I decided to analyze it:
Scope and Tools Used
The following navigation-equipped cars were used for this analysis:
- X5 xDrive40i (2020)

- 120i (2020)

- X1 sDrive20iA X Line (2018)

BMW Connected is a mobile app compatible with 2014 and newer navigation-equipped vehicles (BMW ConnectedDrive). It allows the user to monitor and remotely control some features such as:
- Lock/Unlock
- Location tracking
- Lights
- Horn
- Climate control
- Destinations (navigation system)
- Doors and windows status
- Fuel level
- Mileage
BMW Connected App Demonstration (Youtube)
The latest version of the app available on Apple Store was:
- BMW Connected for iOS v10.6.2.1807
I installed the app on two iPhones, neither of which were jailbroken:
- iPhone XS Max (iOS 13.4.1)
- iPhone 8 Plus (iOS 13.3.1)
Then, I found unencrypted data using the following basic tools:
- Windows 10 Home
- Ubuntu Linux 19.10
- strings
- plistutil
- base64
- jq
Analysis and Results
You’ll see how easy it was to extract and decode the stored data.
Data Stored Unencrypted
The cars were added and authenticated within the app:
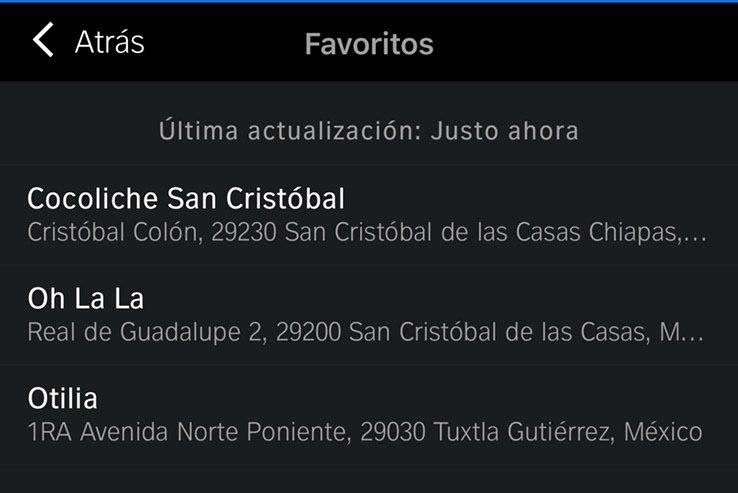
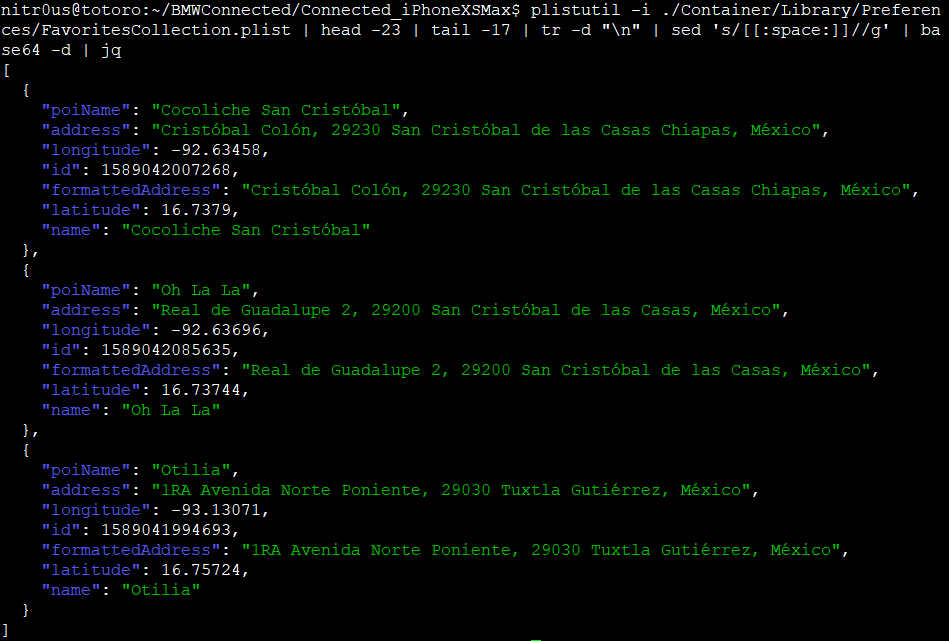
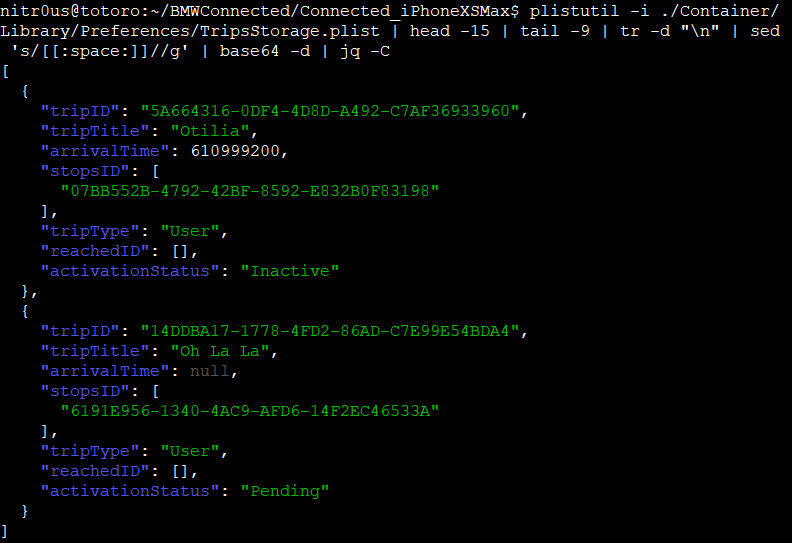
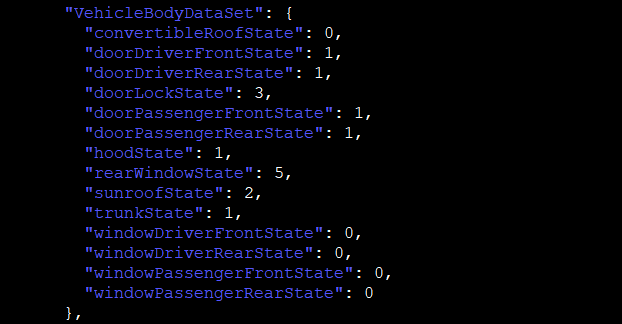
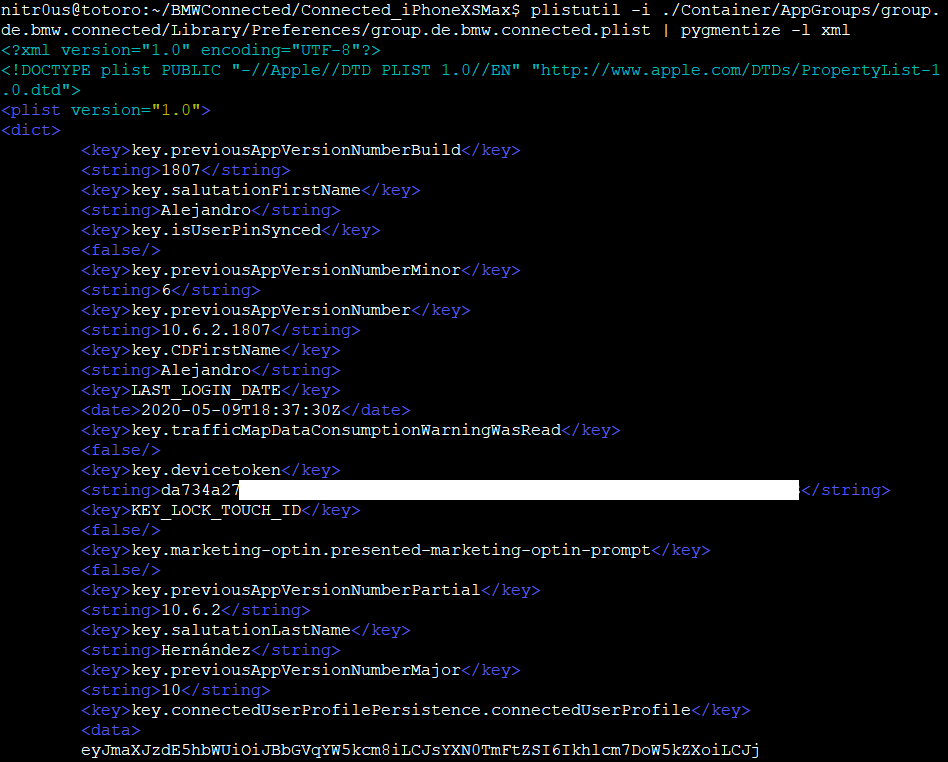
For both installations, the same behavior was observed: data was stored base64-encoded but unencrypted in .plist files. I used the plistutil command to decode such files, then, I piped the output through other command-line tools to strip empty lines and spaces.
Once I had the base64 strings, I decoded them with the base64 tool and finally, formatted and colorized the JSON output with the jq tool:
- Favorite locations (FavoritesCollection.plist)
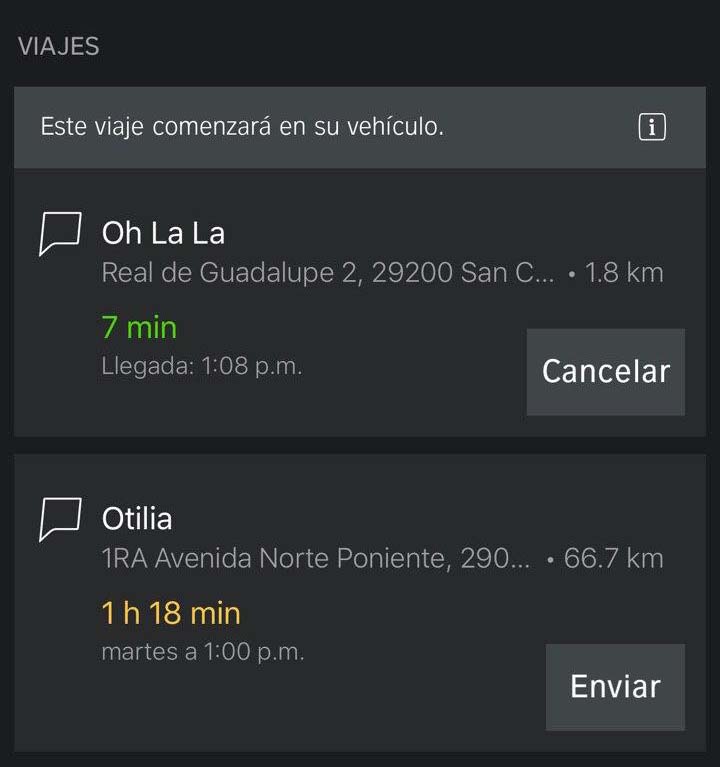
- Directions sent to the vehicle (TripStorage.plist)
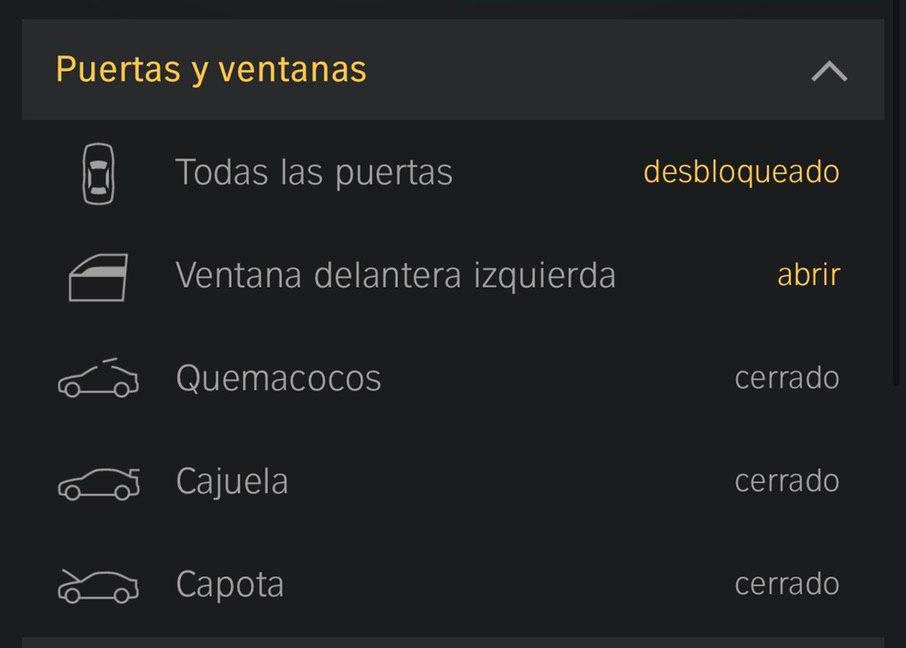
- Status of doors and windows (VehicleHub.Suite.plist)
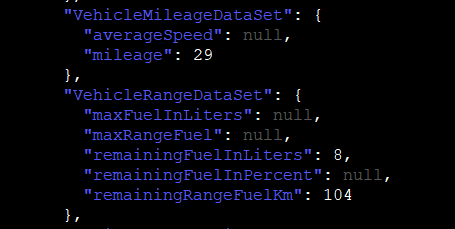
- Mileage and remaining fuel (VehicleHub.Suite.plist)

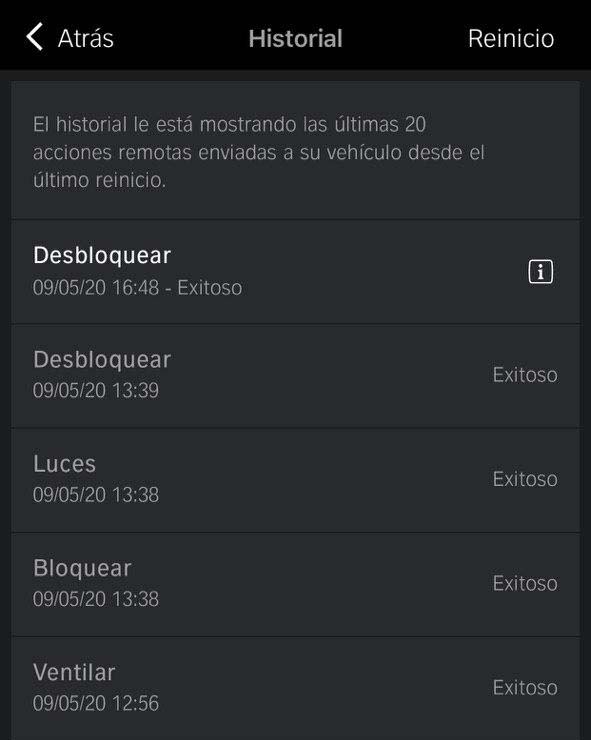
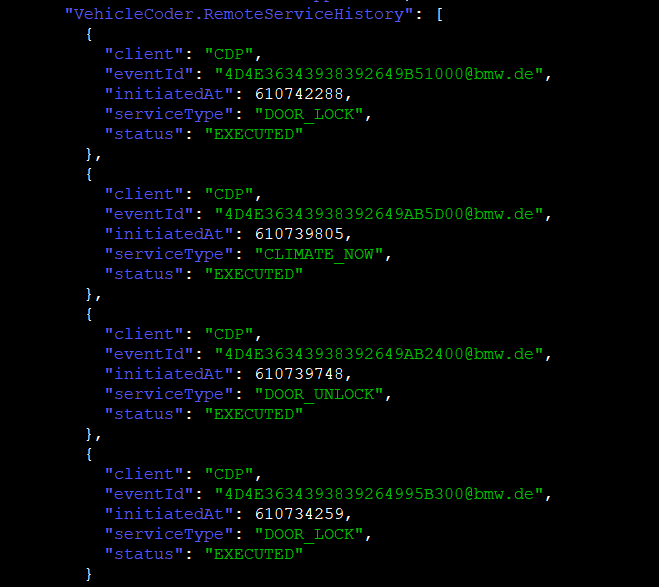
- History of remote actions (VehicleHub.Suite.plist)
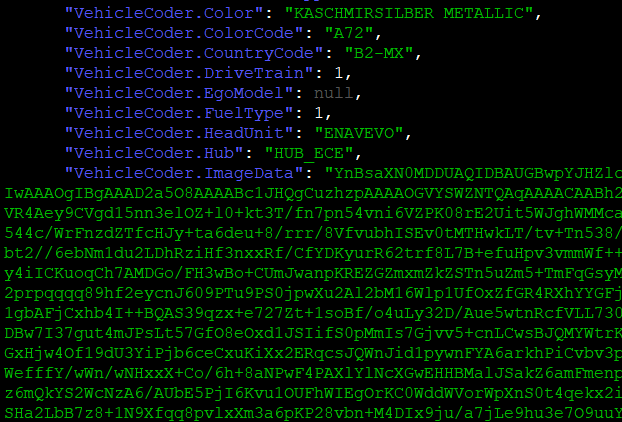
- Car color and picture (VehicleHub.Suite.plist)
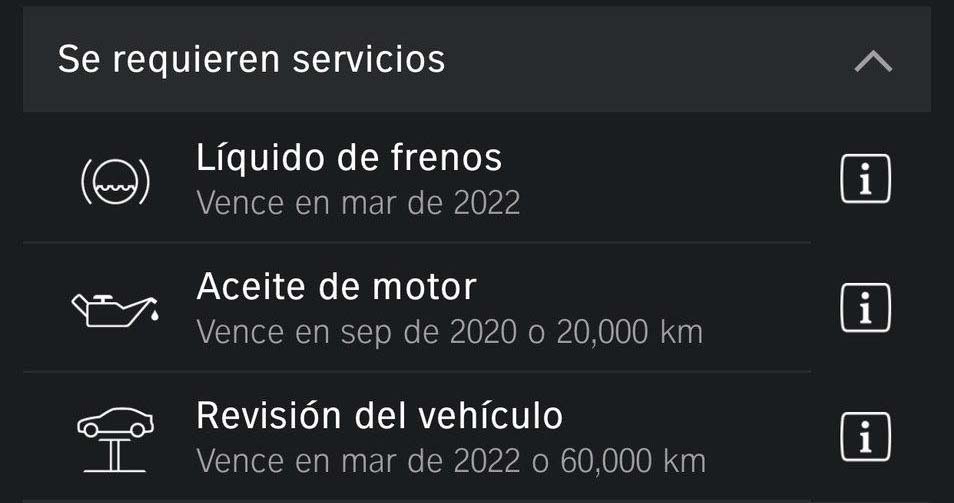
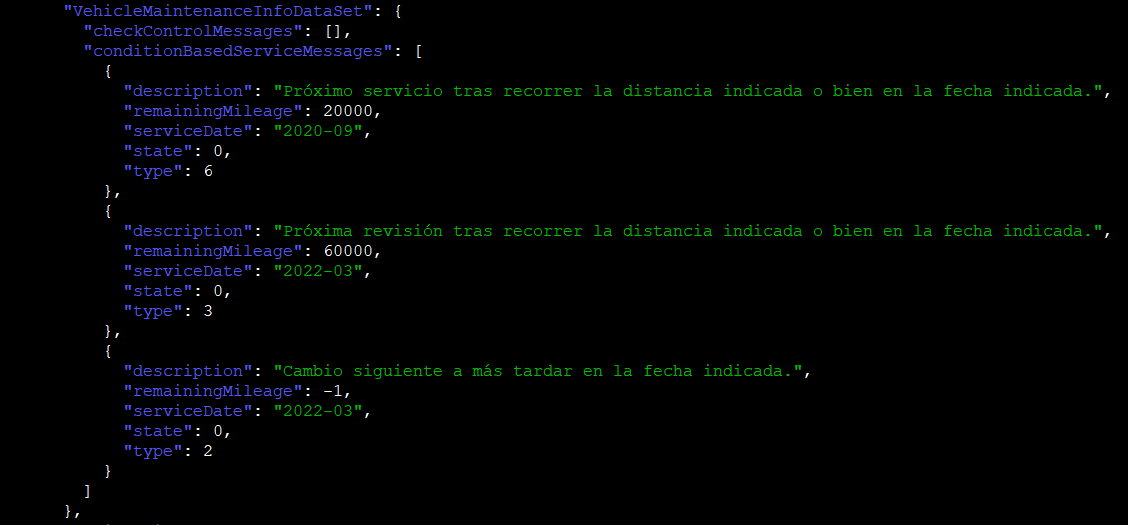
- Next maintenance due dates (VehicleHub.Suite.plist)
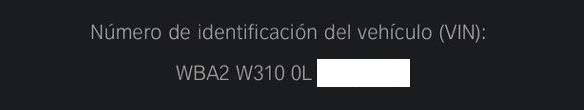
- VIN and model
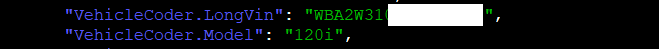
- Owner’s first and last name and last logged date (group.de.bmw.connected.plist)
Weak Password and PIN Policies
On registration, I noticed the password policy only required eight characters from at least two of the following three charsets:
- Letters (abc = ABC)
- Numbers
- Special characters

Such a policy might seem good enough; however, making the password case-insensitive significantly decreases its complexity. During testing, it was possible to login with any of the following passwords:
- Qwerty12
- QWERTY12
- QwErTy12
Also, the app permits users to select an easy-to-guess PIN, which is used to unlock the car or access the app if the smartphone does not implement FaceID, TouchID, or a passcode. The existing PIN code policy allows users to choose weak combinations, such as consecutive numbers (e.g. “1234”) or the same number (e.g. “0000”).

However, the most commonly used feature for authentication is either FaceID or TouchID.
Recommendations
The takeaways are very simple:
- For end-users:
- Only authenticate your phone on trusted computers.
- Avoid connecting and trusting your phone to shared workstations.
- Use complex passwords and PIN codes.
- For developers:
- Do not put your complete trust in the operating system.
- Encrypt sensitive data on your own.
Responsible Disclosure
One of IOActive’s missions is to act responsibly when it comes to vulnerability disclosure.
The following is the communication timeline with BMW Group:
- May 2, 2020: IOActive’s assessment of the BMW Connected App started
- May 15, 2020: IOActive sent a vulnerabilities report to BMW Group following its guidelines
- May 20, 2020: BMW Group replied. They internally sent the report to the responsible departments
- May 26, 2020: IOActive asked BMW Group for any updates or questions and let them know about our intention to write a blog post
- May 28, 2020: BMW Group said to wait for a new app release prior to publishing a blog post and asked for details to include the researcher in BMW Group’s Hall of Fame site
- Aug 07, 2020: BMW Group and IOActive had a call to discuss the technical information that would be published in a blog post
- Aug 13, 2020: BMW Group sent an email explaining how they would fix the issues
- Aug 19, 2020: IOActive sent a draft of the blog post to be published to BMW Group for review
- Aug 24, 2020: BMW Group suggested some modifications
- Sep 08, 2020: IOActive sent the second version of the draft of the blog post to be published to BMW Group for review
- Sep 11, 2020: BMW Group agreed with the final content
- Sep 22, 2020: IOActive blog published.
The Fix
BMW Group’s security statement:
“Thanks to the notification of Alejandro Hernandez at IOActive via our responsible disclosure channel, we were able to change the way the app’s data cache is handled. Our app development team added an encryption step that makes use of the secure enclave of Apple devices, at which we generate a key that is used for storing the favorites and vehicle metadata that Alejandro was able to extract. We appreciate Alejandro for sharing his research with us and would like to thank him for reaching out to us.”
Acknowledgments
I would like to give special thanks to my friend Juan José Romo, who lent me two brand new cars for testing.
Also, I’d like to thank Richard Wimmer and Hendrik Schweppe of BMW Group for their quick response and cooperation in fixing the issues presented here.
Thanks for reading,
Alejandro @nitr0usmx


